Bookmarks
Content
- Content
- Awesome Awesomeness
- Pentest linux distributions
- Methodologies
- Courses and certifications
- Vulnerabilities register
- Interesting bookmarks
Awesome Awesomeness
Infosec_Reference (github source) - “an information security reference that doesn’t suck”
National Security Agency github - national security agency proposals on enhansing future world’s security
- bayandin/awesome-awesomeness
- sbilly/Awesome Security
- yeyintminthuhtut/Awesome Red Teaming
- misterch0c/Awesome-Hacking
- onlurking/awesome-infosec
- enaqx/awesome-pentest
- vitalysim/Awesome-Hacking-Resources
- sunnyelf/awesome-hacking
- offensive security, 1400 articles
- SANS posters
- coreb1t/awesome-pentest-cheat-sheets - collection of the cheat sheets useful for pentesting
- SecWiki/sec-chart (chinese)
- pentest-bookmarks (code.google.com) (pentest-bookmarks (exported to github))
- Offensive Security Bookmarks
Binary:
- REMath/literature_review - collection of program analysis research with a focus on machine code (binary)
REMath/implementations
- Infrastructure PenTest Series: Part 1 - Intelligence Gathering
- Infrastructure PenTest Series: Part 2 - Vulnerability Analysis
- Infrastructure PenTest Series: Part 3 - Exploitation
top vulnerabilities
security groups
- OWASP, OWASP Testing Guide v4, OWASP Cheat Sheet Series
owasp russia: owasp russia, owasp russia presentations (owasp russia on slideshare) - WASC - The Web Application Security Consortium
- defcon
defcon russia: defcon russia, DefconRU
studying
-
CTF:
- ctf field guide
- О CTF (kmb.ufoctf.ru) (RU) - about ctf, and various technologies/utilities
- ctfs writeups
-
Web:
BugBounty-related articles
- Advice for Writing a Great Vulnerability Report
- Writing a bug report - Attack Scenario and Impact are key!
Pentest linux distributions
Distro Tools List - list of security linux destributives
Лучшие дистрибутивы для проведения тестирования на проникновение
- kali linux (+ exists kali for android - NetHunter) - penetration testing and ethical hacking linux distribution (xfce - looks like the most lightweight)
- ptf - The PenTesters Framework (PTF) - a way for modular support for up-to-date tools
-
Other pentest distros:
- BlackArch - concept: contain everything
- Parrot Security OS - good kali alternative
- Backbox (ubuntu-based)
- Devuan, pentoo, bugtraq, Cyborg, Matriux, ArchAssault
- samurai - targeted at web-pentest
- NST (Network Security Toolkit)
- Wifislax; airslax; Xiaopan OS - wifi security
- Santoku linux; Android Tamer - targeted at mobile security
- DEFT linux - a linux distribution for computer forensics
- pentestbox - collection of hacking tools for windows
- osboxes.org - prebuilt OS
- tb.rg-adguard.net - microsoft products
Caution! - hackers hack other hackers - divide your personal accounts/environment and your working pentest env.
Caution! - Kali linux, etc. has a lots of built-in tools, which is not really thoroughly checked for vulnerabilities, therefore all hacking destributions is highly dangerous.
Methodologies
Penetration testing methodologies (owasp):
- PTES - Penetration Testing Execution Standard (похожа на ISO 27001)
- OSSTMM - Open Source Security Testing Methodology Manual
Formalized and structured document. It includes security testing, security analysis, operational security metrics, trust analysis, operational trust metrics, the Möbius Defense, and the essential tactics for testing the security of anything. Contains detailed, stage-by-stage description of penetration testing process. - ISSAF - Information Systems Security Assessment Framework
- NIST SP 800-115 - Technical Guide to Information Security Testing and Assessment (2008)
- ISO/IEC 27000-series
Государственные стандарты РФ
ГОСТ Р ИСО МЭК 15408-1-2012 / ГОСТ Р ИСО МЭК 15408-2-2013 / ГОСТ Р ИСО МЭК 15408-3-2013 - FedRAMP Penetration Test Guidance
-
Bank’s standarts:
- PCI DSS - Payment Card Industry Data Security Standard - PCI document library
PCI Penetration Testing Guidance (march 2015) - ISO/IEC 27001:2013 Информационные технологии. Методы защиты. Системы менеджмента информационной безопасности. Требования
- РС/СТО БР ИББС-2.6-2014 - семейство стандартов банка россии. есть требования по аудиту, оценке, сбору и анализу данных, по оценке рисков ИБ, обеспечению ИБ на стадии жизненного цикла.
- PCI DSS - Payment Card Industry Data Security Standard - PCI document library
-
Защита перс. данных и прочей информации, не составляющей гос. тайну:
- Приказ ФСТЭК России от 18 февраля 2013 г. N 21 - о необходимости проведения тестирования на проникновение
- Приказ ФСТЭК России от 11 февраля 2013 г. N 17 - о необходимости проведения тестирования на проникновение
Attacks-centered methodologies:
-
Web-applications only:
- OWASP testing guide
- TIDoS-Framework - The Offensive Web Application Penetration Testing Framework
- Web application hacker’s handbook. Chapter 21. Web application hacker’s methodology.
- ATT&CK/ATTACK - Adversarial Tactics, Techniques & Common Knowledge
- Penetration Testing Framework
- SANS: 20 critical security controls you need to add
- TBHM - The Bug Hunters Methodology
Courses and certifications
Diagram. Choosing the certificate:
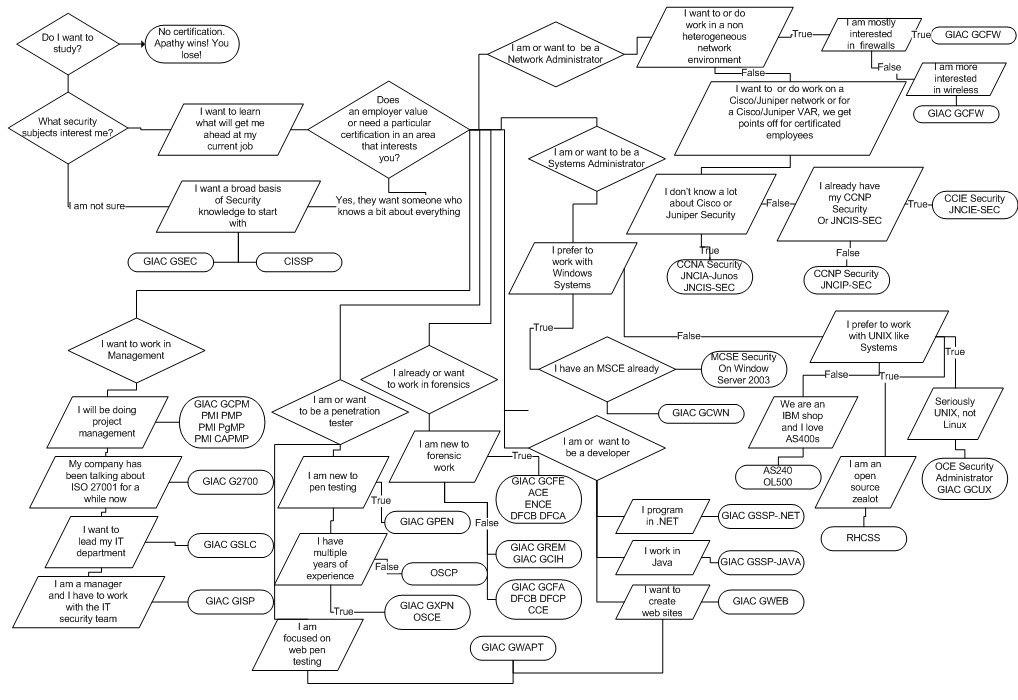
Certifications:
-
Executive certifications:
Сертификация специалистов по ИБ / Международные сертификаты специалистов по ИБ / Курсы по информационной безопасности
(open spoiler for comparison chart)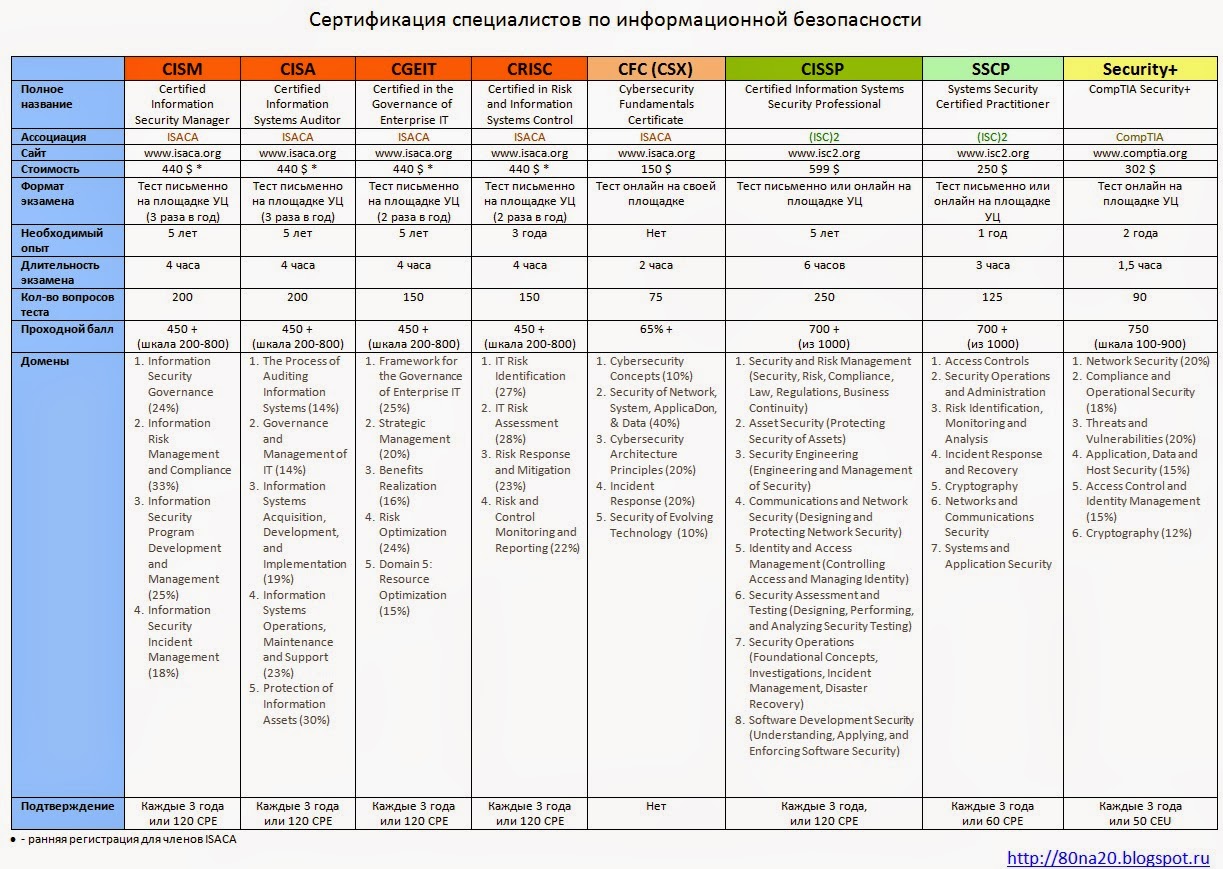
- ISACA: CISM, CISA, CGEIT, CRISC, CFC(CSX)
- (ISC)2: CISSP, SSCP
- COBIT 5 for Information Security (COBIT 5 - framework for the governance and management of enterprise IT) (recommended for understanding for technical directors)
- CompTIA Security+
- ISO/IEC 27001 Lead Auditor, ISO/IEC 27001 Lead Implementer
-
Pentest Certifications (not executive) (aug 2018)
List of computer security certifications (wikipedia)some industry recognised standards: Tiger Scheme, CHECK and CREST * SANS courses&prices / SANS courses / SANS find training
CERTCOLLECTION - BASELINE - SANS & Offensive-Security (2017) (torrent - 85 GB) * CREST professional qualifications * Tigerscheme * CHECK penetration testing - cisco certifications, CCNA -> CCNP -> CCIE
- Certificate of Cloud Security Knowledge (CCSK)
Career paths:
Some examination mediators:
- CBT Nuggets
- infosecinstitute
- IACRB
- iapp
- edu.softline.ru
- www.specialist.ru (при Бауманке)
Courses:
- onlurking/awesome-infosec - a curated list of awesome infosec courses and training resources
About some courses:
- OSCP (Offensive Security Certified Professional) - mainly internal perimeter
All that things I need to pass OSCP / Как я сдавал OSCP (хабр) (RU) - CISSP (Certified Information Systems Security Professional)
CISSP подготовка: https://habrahabr.ru/company/pm/blog/330984/ https://habrahabr.ru/company/it/blog/196638/
Vulnerabilities register
CVE - Common Vulnerabilities and Exposures
CWE - Common Weakness Enumeration specification
CPE - Common Platform Enumeration (official dictionary)
- CWE - by NVD, by mitre
- CVSS v2 - common vulnerability scoring system
- NVD - national vulnerability database
- CVE - common vulnerabilities and exposures
cve.mitre downloads - OVAL - open vulnerability and assessment language
- snyk.io - this site can be google-dorked for vulnerabilities, e.g.
jquery site:snyk.io
Interesting bookmarks
Cryptography:
- Not so random numbers. Take two - attack on random numbers generator
Network:
- (RU) Атакуем DHCP - хорошее описание работы протокола DHCP
Reverse:
Unclassified
Hack Android using metasploit without port forwarding over internet - 2017
(RU) Атака на беспроводные сети Wifi. Чуть меньше теории и чуть больше практики (хабр)